CSPM Definition
Cloud Security Posture Management (CSPM) identifies and mitigates risk by automating visibility, continuous monitoring, threat detection, and remediation workflows across diverse cloud environments/infrastructure, such as:
- IaaS (Infrastructure as a Service)
- SaaS (Software as a Service)
- PaaS (Platform as a Service)
Risk visualization and risk assessments are only two of the many things that CSPM can do for you. CSPM tools can also respond to incidents, recommend remediation, monitor compliance, and integrate DevOps into hybrid and multi-cloud environments/infrastructures. Some CSPM solutions assist security teams in proactively identifying and remediating weak spots in cloud environments before a breach occurs.
What is the Significance of CSPM?
As more people and organizations migrate to the cloud, so do the number of intentional and unintentional security risks. While data breaches are common, the majority of errors are still caused by cloud misconfigurations and human error.
Threats to cloud security configuration and infrastructures, as well as the growing possibility of unintended exposure, can take many forms. A robust and diverse CSPM can defend you and your organization against the following:
- Misconfiguration
- Concerns about legal and regulatory compliance
- Unauthorized entry
- APIs and interfaces that are not secure
- Account stealing
- Inadequate visibility
- Lack of clarity in the project responsibility timeline
- External data exchange
- Identity and cloud entitlement misuse and configuration
- Issues of Compliance and Regulation
- Attacks on denial of service (DoS) and distributed denial of service (DDoS)
The Advantages of CSPM
Securing your workloads begins with implementing customized security policies for your organization using a comprehensive, powerful CSPM. These are the four primary advantages of CSPM:
- Give You More Power: Manage your cloud security policies and ensure compliance of your PaaS services and virtual machines with changing regulations.
- Simplify and Connect Cloud Security Posture Management: Launch and configure CSPM across large-scale environments using AI and automation to quickly identify threats.
- Always Be Alert: Your CSPM monitors the security of your cloud resources in various environments, such as Azure, AWS, and Google Cloud.
- Offer Assistance and Recommendations: Get insights into your current situation as well as recommendations for improving your security posture.
How do Cloud Infrastructure Security Tools Work?
Cloud misconfiguration occurs when the security framework of a cloud infrastructure does not adhere to a configuration policy, putting the infrastructure's security at risk. CSPM provides visibility across cloud environments, allowing you to quickly detect configuration errors and automate their resolution.
CSPM tools manage and mitigate risk across an organization's entire cloud attack surface by using the following methods:
- Visibility
- Constant monitoring
- Detection and mitigation of threats
- Workflows for restoration
- Strengthening guidance
Important CSPM Capabilities
Important capabilities of CSPM tools include:
- Using automation capabilities to make immediate corrections without human intervention.
- Monitoring, assessing, and managing IaaS, SaaS, and PaaS platforms.
- Detecting and automatically correcting cloud configuration errors.
- Examining regulatory compliance mandates such as HIPAA, PCI DSS, and GDPR.
Configuration Wizard
The Configuration Wizard is a tool in Prancer that allows users to create configuration files without needing to write any JSON manually. It supports a variety of providers such as Azure Cloud and AWS Cloud, as well as IaC (Infrastructure as Code) tools like IaC Github Enterprise and IaC Azure DevOps. Before starting the configuration process, users must specify a unique Collection Name. The wizard provides step-by-step instructions on how to configure each provider.
Configuration Wizard provides an easy way to create configuration files without writing any JSON Configuration manually.
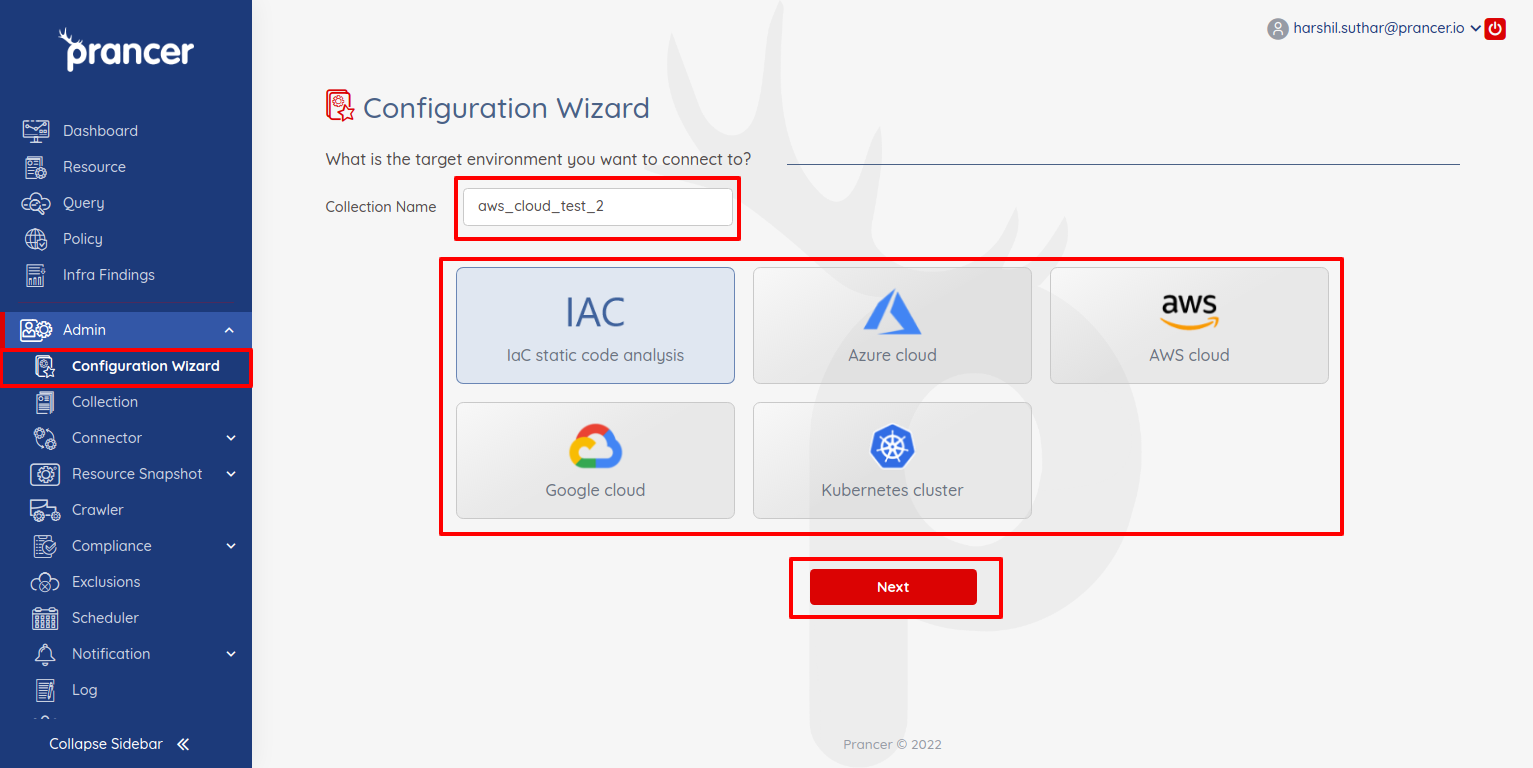
- In the wizard screen, users can see a list of providers supported by Prancer.
- Users can select one of the providers at a time to create configurations. Before starting the configuration, the user has to specify the Collection Name.
- The collection Name should be unique. If it already exists, then it will show the error message.
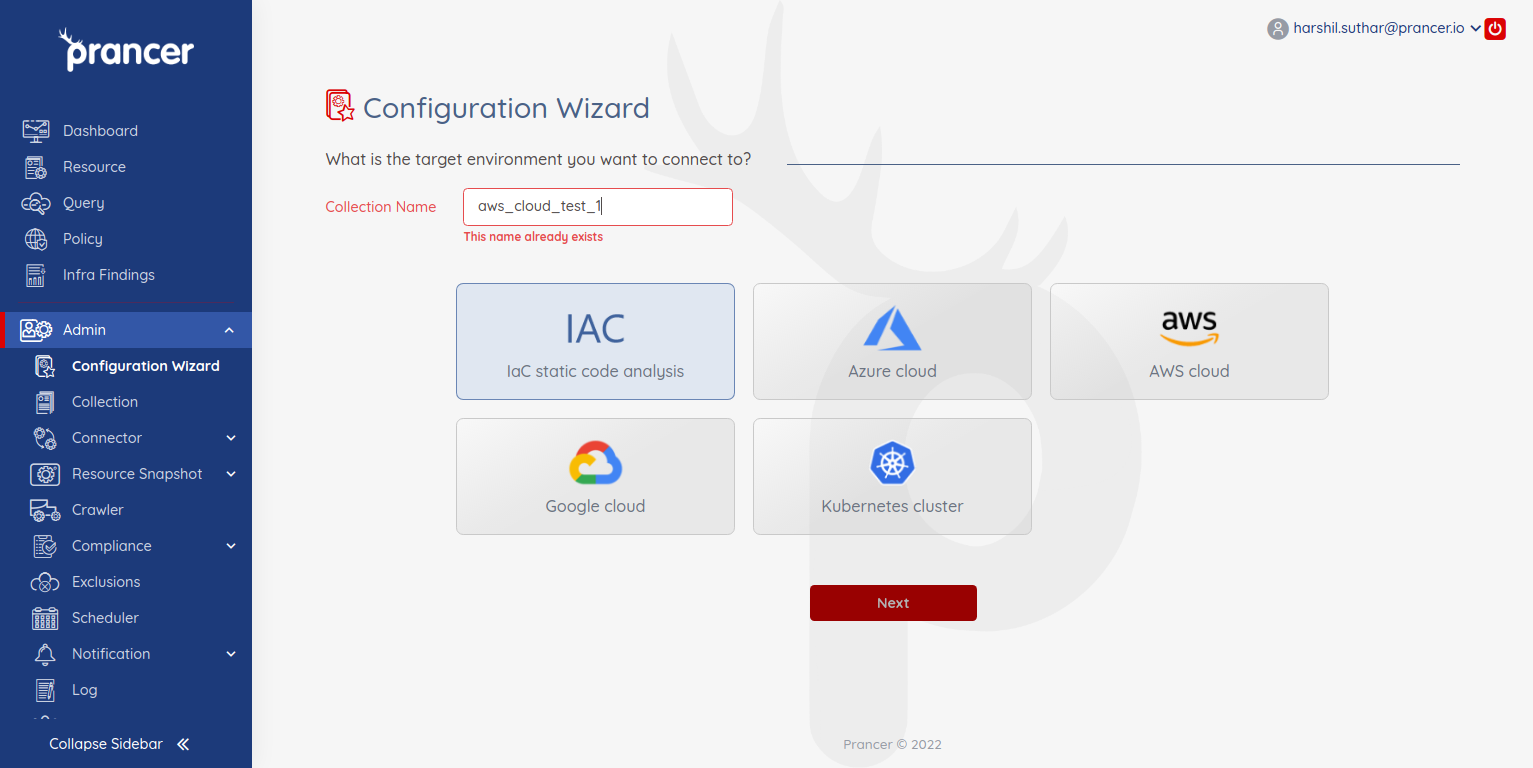
Check how to configuration for each of the following providers: