PAC Custom Scripts - Parameters and Secrets
Overview
This section explains how to use parameters and secrets in custom attack scripts for PAC. The scripts can be written in Python or Javascript and may require parameters like URLs, form data, and header information or secrets like passwords and account IDs. To handle these requirements, PAC provides mechanisms to securely and accurately feed this data at runtime. The scripts can have placeholders for parameters that can be replaced by values in a metadata file or PAC configuration file. Secrets can also be replaced by key-vault values stored securely in the Prancer web portal. The module includes code examples and screenshots to illustrate the process of using placeholders, metadata files, configuration files, and key-vault values.
Custom Attack Scripts in PAC can be written in Python or Javascript. The logic of the attack in the scripts shall need parameters and secrets. In some scenarios for these custom attack scripts, parameters in the form of variable URLs, form data format, header information and in other cases parameters in the form of secrets like passwords, accountIds shall be required. To facilitate the above requirements, PAC infrastructure provides mechanisms to feed these data at runtime securely and accurately.
Parameter Data values and Secret keys
The logic of the attack in the scripts shall need parameter values. Parameters are publicly shareable and can change based on the application. These can be put in the scripts as hard coded values, in that case the script becomes usable for only one application.
Hence the scripts can have placeholders for parameters. The parameter values can be placed in metadata file and committed to the repository at the same level as the script is committed. The parameter values can also be placed in the PAC configuration file. The parameters shall be key-value map and shall be replaced by PAC before loading the script to scanner. Every occurrence of the key shall be replaced with the value in the script.
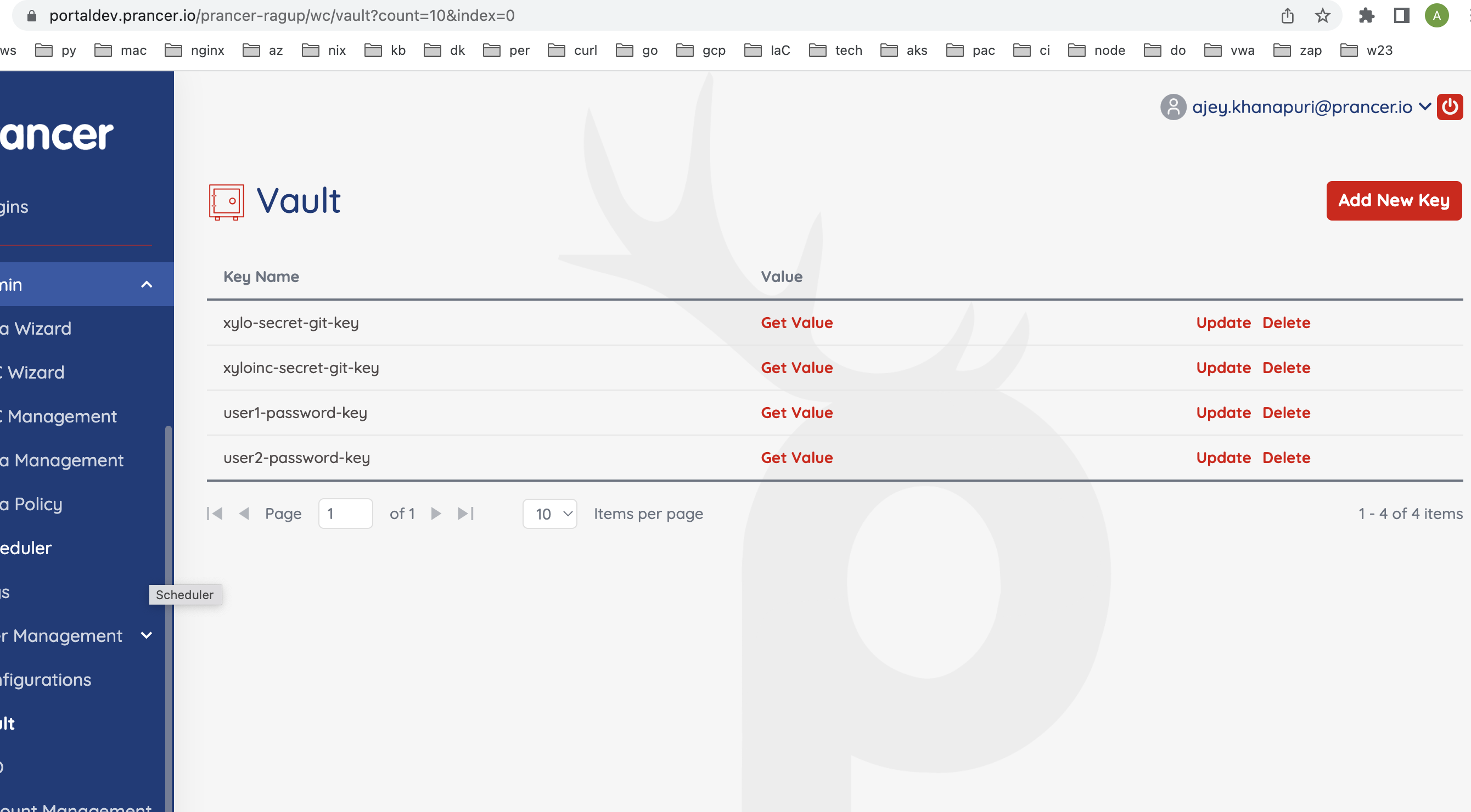
The secrets also are key-value map, but the value is the key to the key vault secret stored in the prancer web portal securely. At the point of loading of the script, the values are fetched from the key-vault, replaced and then the script loads to scanner.
In a rare occasion when parameters and secrets have the same key, the secrets will override the parameter values. In the error scenario when there any placeholders left in the script, the PAC shall NOT attempt to load the script to ZAP as the script will give erroneous results for the script run
- Placeholders in the scripts in {{}}
import os
import json
import org.parosproxy.paros.network.HttpRequestHeader as HttpRequestHeader
import org.parosproxy.paros.network.HttpHeader as HttpHeader
import org.parosproxy.paros.network.HttpMessage as HttpMessage
from org.apache.commons.httpclient import URI
ROOT_URL = "{{url}}"
USER1_USERNAME = "test1@mailinator.com"
USER2_USERNAME = "test2@mailinator.com"
USER1_PASSWORD = "{{user1password}}"
USER2_PASSWORD = "{{user2password}}"
LOGIN_URL = "{{url}}rest/user/login"
BASKET_URL = "{{url}}rest/basket/6"
LOGIN_PAYLOAD_1 = "email"
.......
....... contd....
- Parameter values and secret keys in metadata yaml file.
Name: Privileage Escalation
Type: active
Engine: jython
Description: Privilege escalation means an attacker gains access to privileges they are not entitled to by exploiting a privilege escalation vulnerability in a target system or application, which lets them override the limitations of the current user account. Privilege escalation is a common way for malicious users to gain initial access to a system.
Charset: UTF-8
Parameters:
url: http://prancersampleapp01.eastus2.cloudapp.azure.com:8008/
Secrets:
user1password: user1-password-key
user2password: user2-password-key
- Parameter values and secret keys in PAC configuration file.
Target: http://demo.testfire.net/
WebScan:
AjaxSpider: false
CVE:
- Path:
Include:
- webserverfingerprinting
Exclude: []
Connector: xylo_github_connector
Parameters:
url: http://prancersampleapp01.eastus2.cloudapp.azure.com:8008/
Secrets:
user1password: user1-password-key
user2password: user2-password-key
- Secret values stored in the vault through the Prancer portal