Report Generator
Introduction
The Report Generator simplifies the process of creating reports by generating HTML report files from editable HTML templates. We provide a customizable HTML template, which users can apdapt. This template is then used to generate dynamic reports based on certain fields. After making desired modifications, users can upload the template to the platform and it will be avaiable in every pac file in that collection.
HTML Template Customization
You will be provided with an HTML report template that you can edit to specify the report's severity or other parameters. The part users will need to edit is -
<!-- User can specify severity condition here -->
{{if or (eq $value.Risk "critical") (eq $value.Risk "high")}}
<div class="page">
Dynamic Reports
How to use the Dynamic Reporting feature
-
Go to the Inventory Managment page.
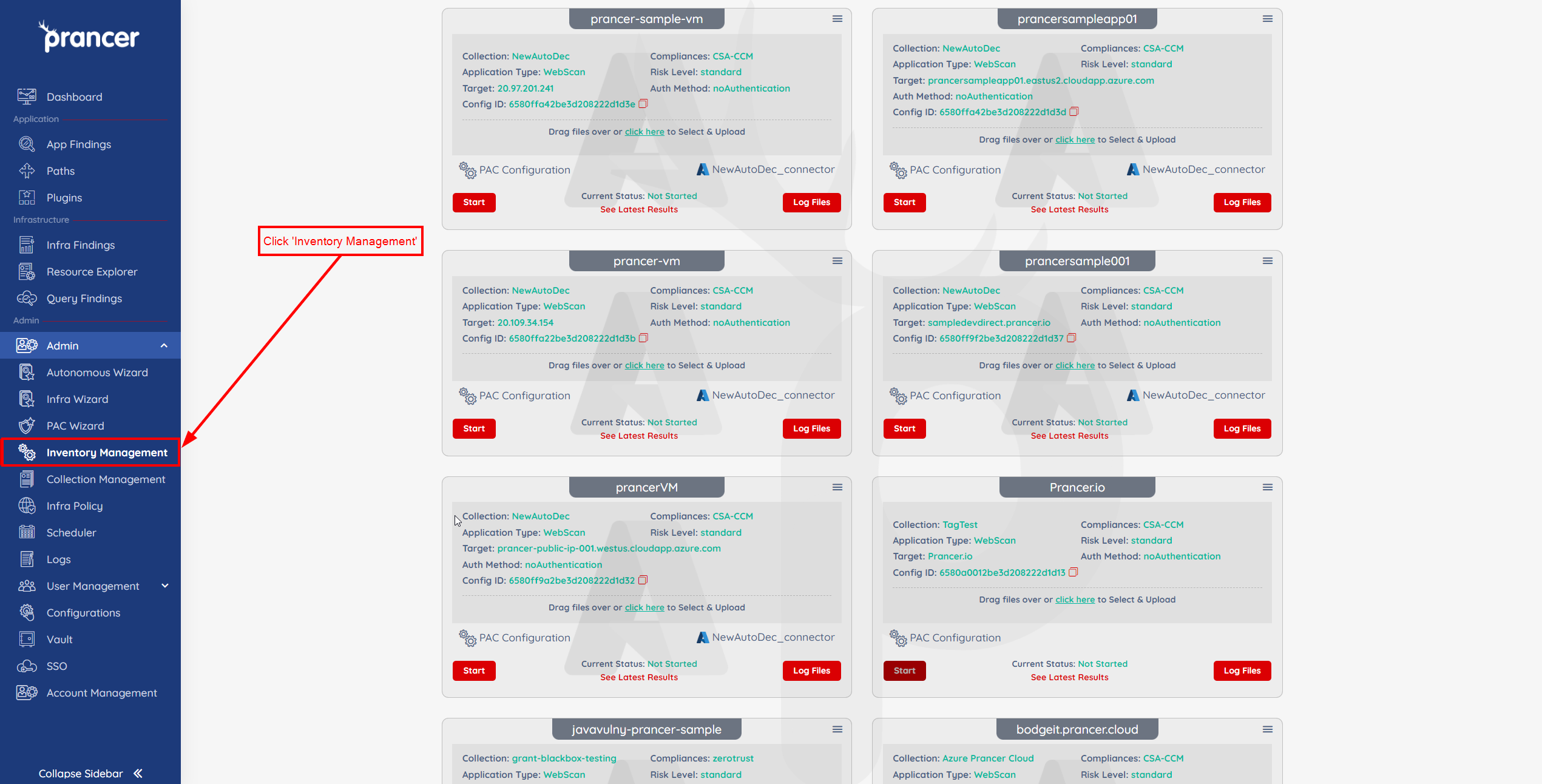
-
Click on the collapsed sub-menu icon and then select Report Templates.
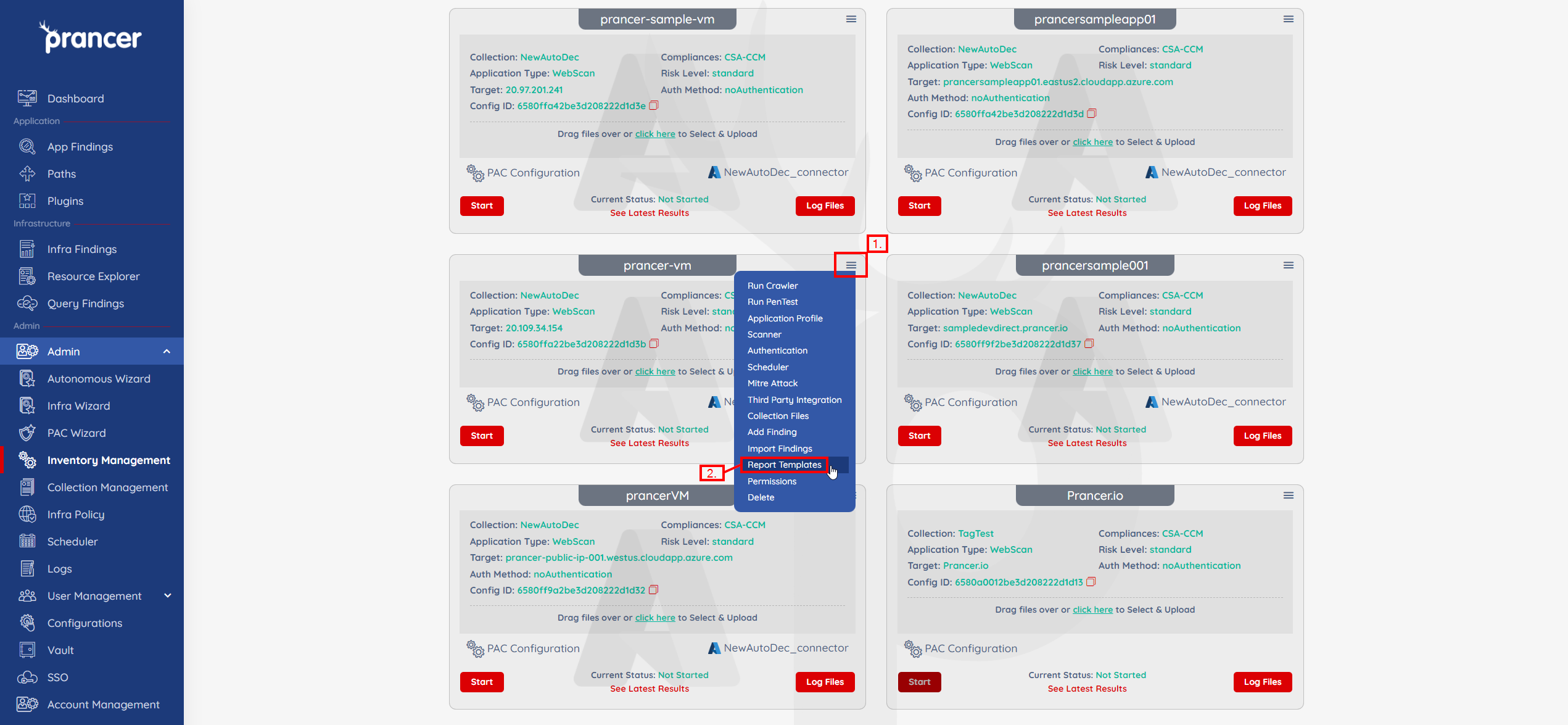
-
Download the default template file using the download button and proceed to make any necessary changes based of the earlier section.
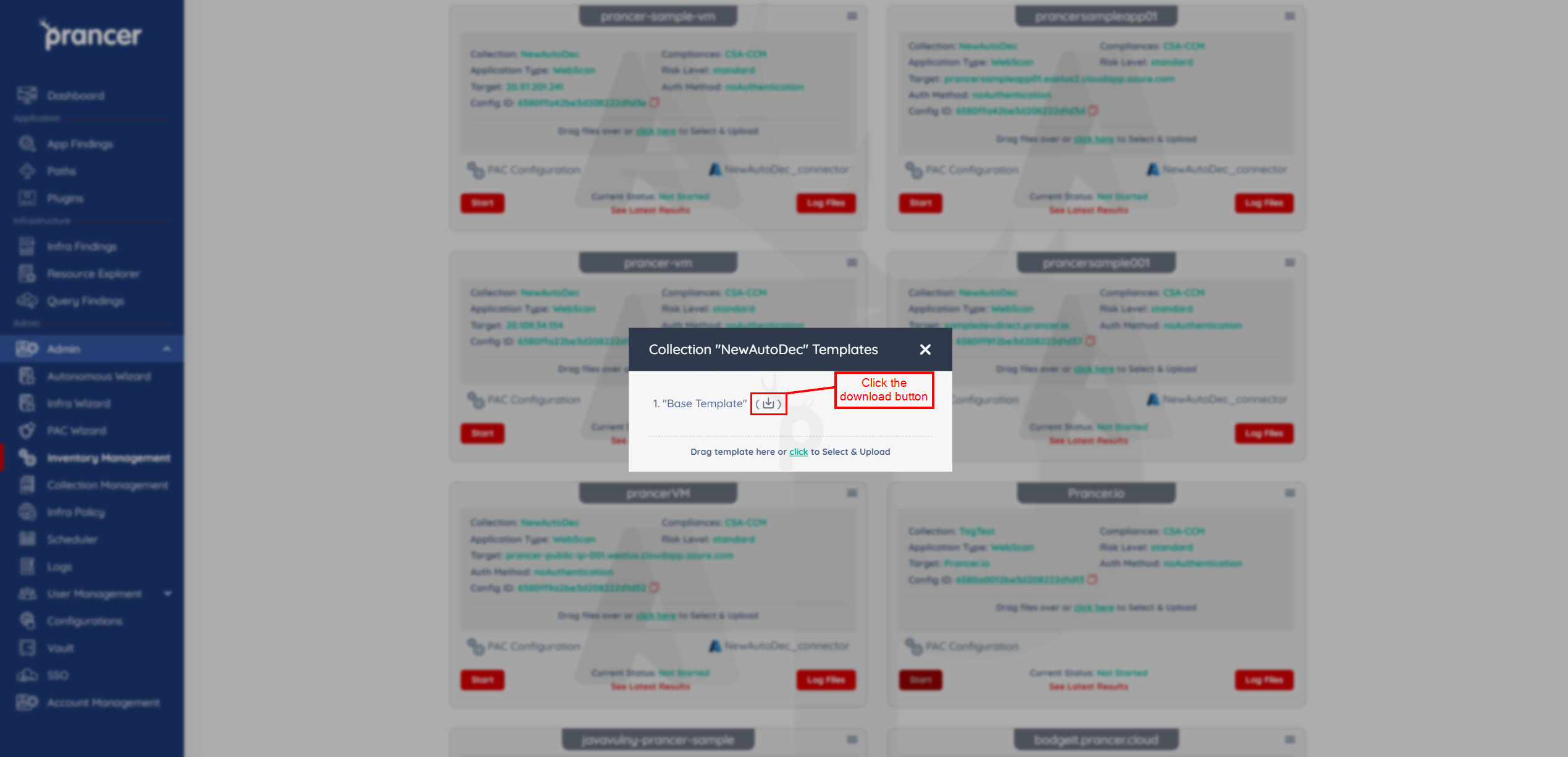
-
Upload your new template file by selecting it or using the drag and drop feature. This template file will now be available in every PAC file that resides in the same collection. Any previously uploaded templates can be downloaded, updated or deleted using one of the three icons listed alongside the template.
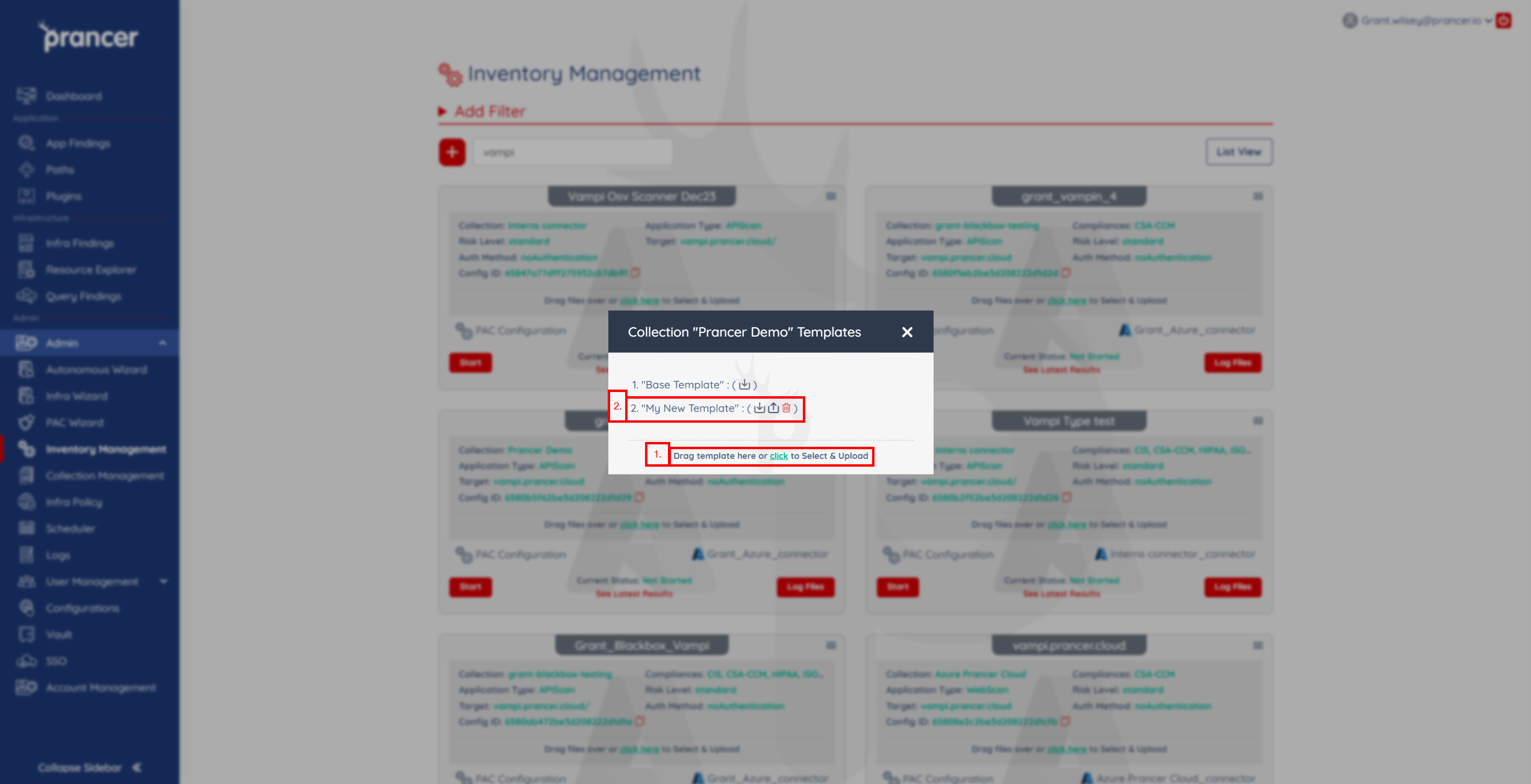
-
To generate a new report with this template, navigate to the Application Security Findings page of your PAC file by clicking See Latest Results.
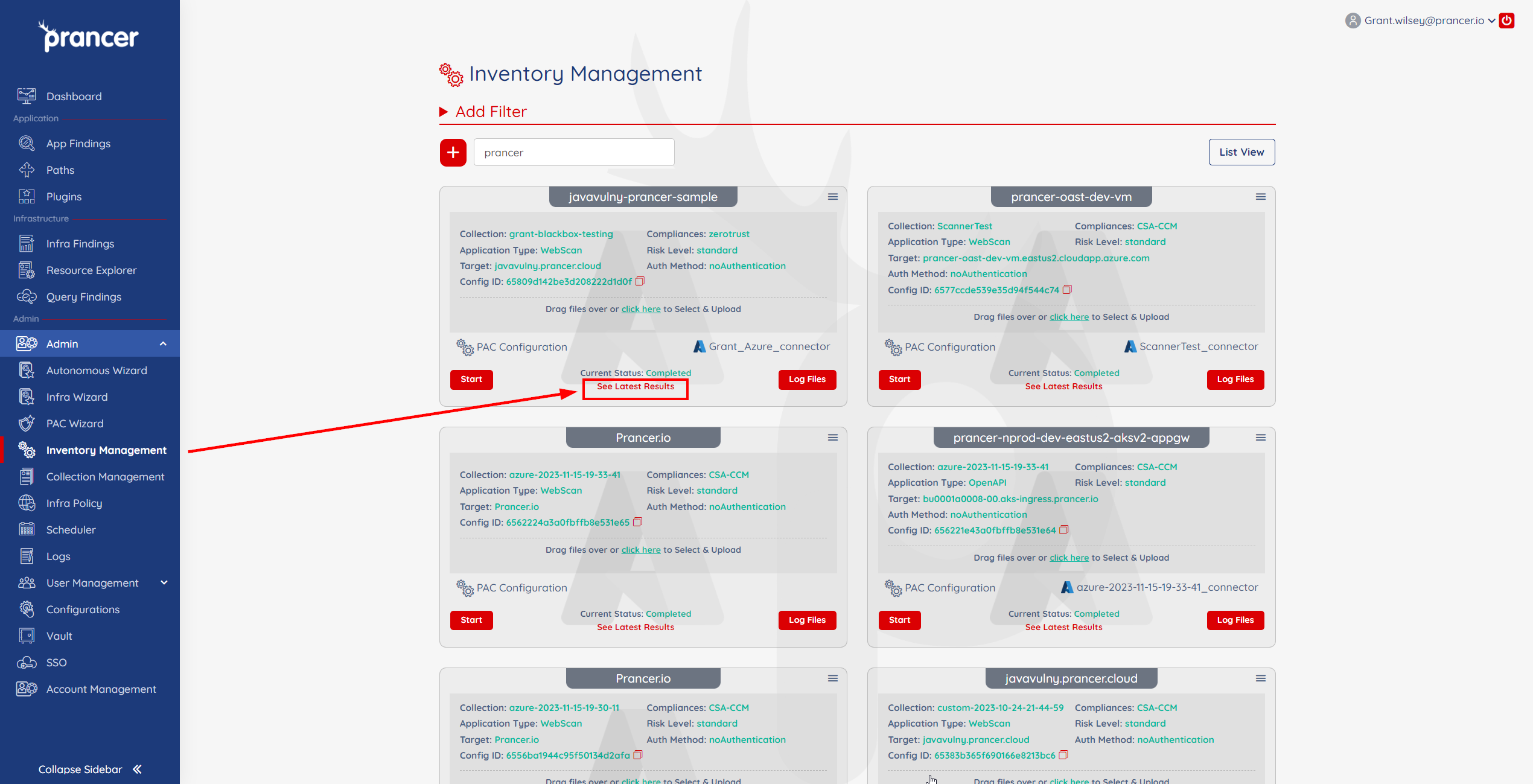
-
From the Findings page, click the Download option to the right and then choose Download Pac Report from the dropdown menu .
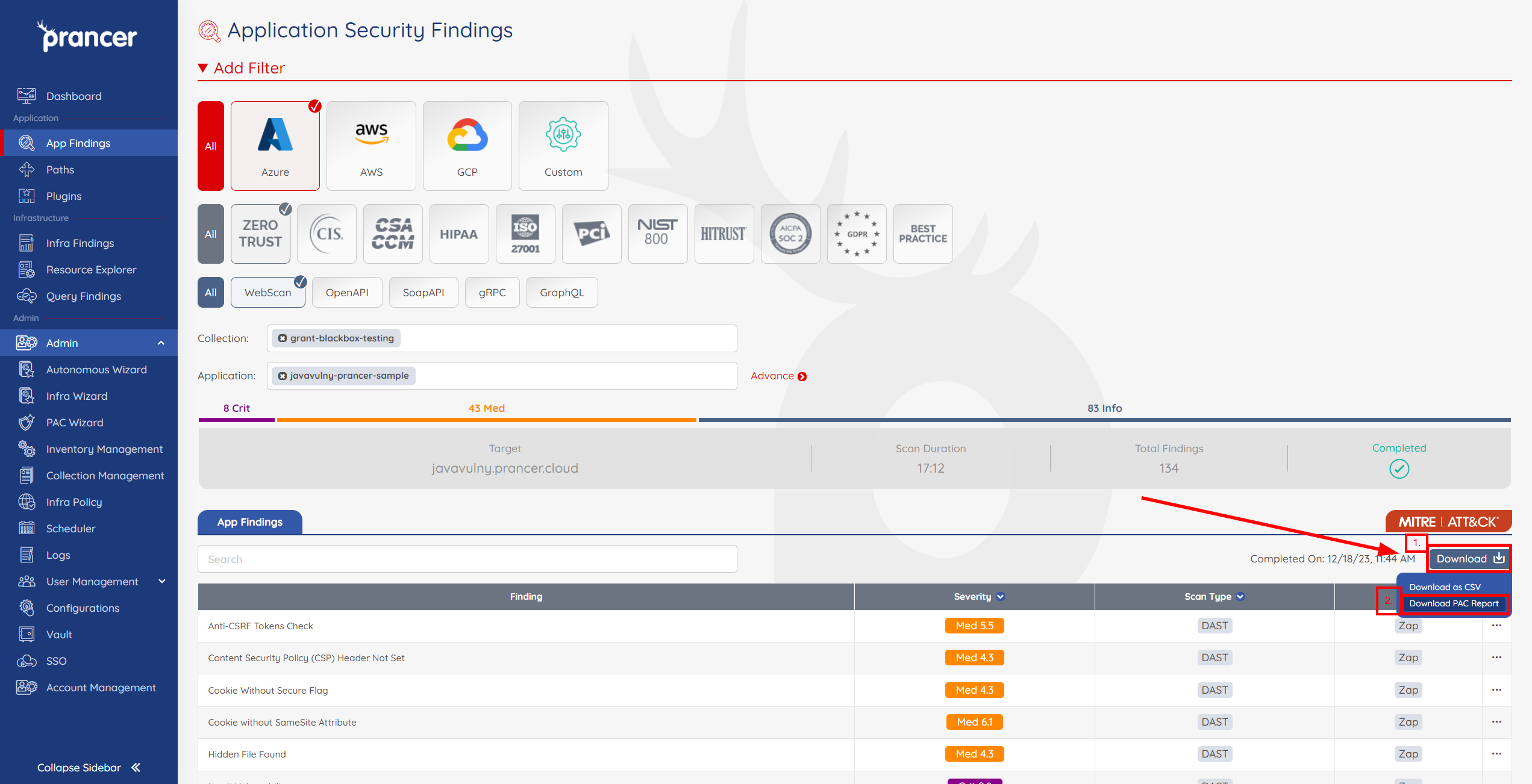
-
The report is ready! Choose Generate Report on your new template to begin downloading. The provided report will now be formatted with your updates to the base template.
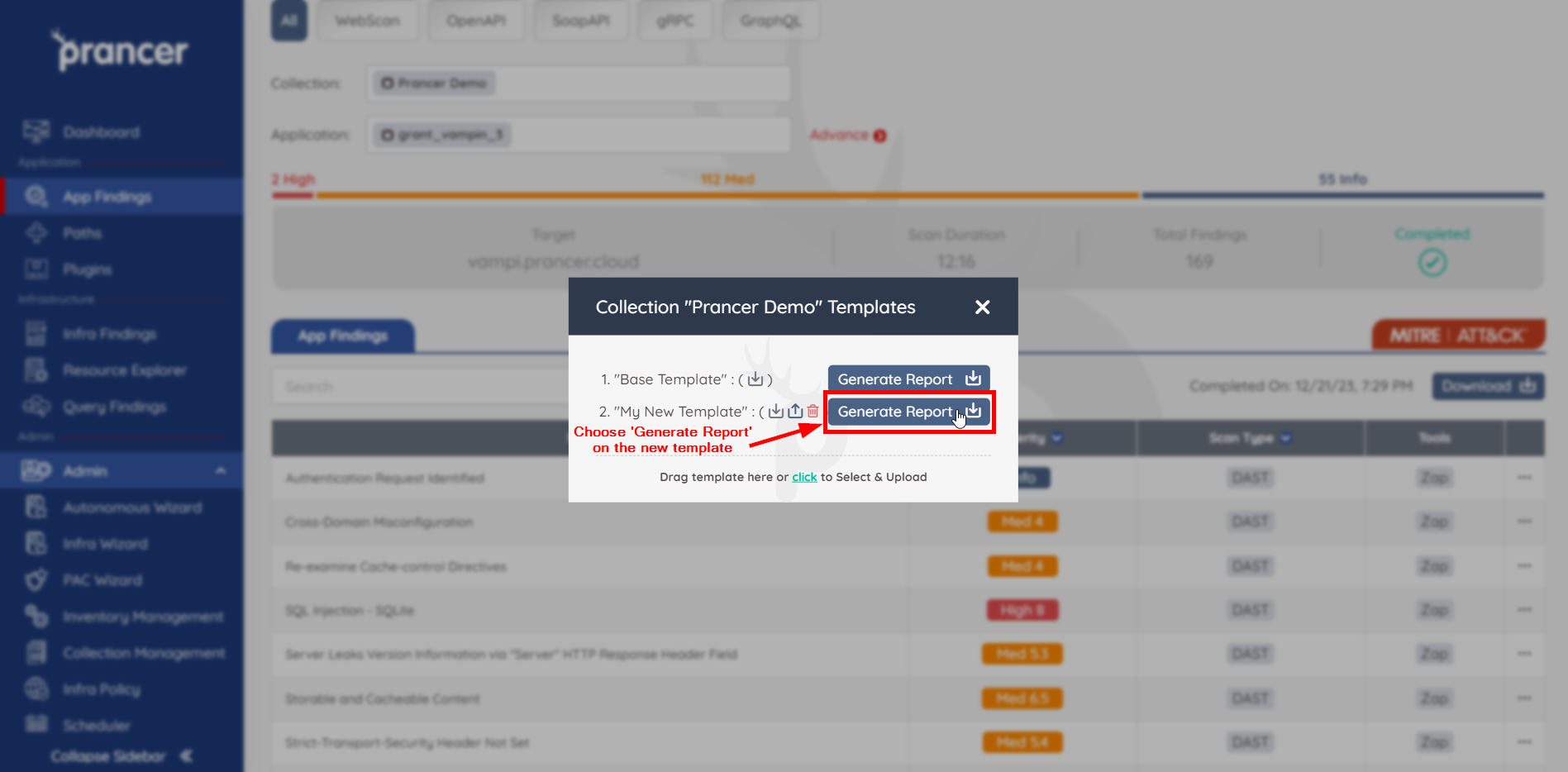
This approach with provided HTML templates enhances flexibility and ease of use in customizing and generating reports, tailored to your specific requirements.