What is CVSS Scoring
The Common Vulnerability Scoring System (CVSS) v3.0 is a standardized framework for evaluating the severity of security vulnerabilities in software and hardware systems, allowing organizations to prioritize their security efforts. It assesses a variety of factors, including the potential impact on system confidentiality, integrity, and availability, the complexity of the attack, and the level of access required to exploit the vulnerability. Consideration is also given to any mitigating factors. Vulnerabilities are scored on a scale of 0 to 10, with higher scores signifying greater severity, and the scores are adjustable over time and context using base, temporal, and environmental metrics. Hence, CVSS v3.0 offers a uniform and objective method for severity assessment of security vulnerabilities to facilitate informed decision-making.
How to Calculate
You can calculate CVSS score using this link NVD - CVSS v3 Calculator
Prancer Integration
Below is an example of the methodology for how Prancer PAC calculates CVSS scoring for each vulnerability found from the pentest.
{
"cweid": "CWE-829",
"cvss_score": 6.1,
"name": "Cross-Domain JavaScript Source File Inclusion",
"mitreId": "T1170"
}
The calculation for the CVSS v3 score is as follows:
- Attack Vector (AV): Network (N)
- Attack Complexity (AC): Low (L)
- Privileges Required (PR): None (N)
- User Interaction (UI): Required (R)
- Scope (S): Unchanged (U)
- Confidentiality (C): Low (L)
- Integrity (I): Low (L)
- Availability (A): None (N)
Using these metrics, the CVSS v3 base score is calculated to be 6.1 (Medium).
As the vulnerability is not exposed to the public internet,the risk profile of the application is Medium, compliant
with zero trust and CIS,and hosted on Azure cloud in a VNET with other cloud resources.Additional controls such as
network segmentation, access controls, and monitoring will further mitigate the risk associated with the vulnerability.
| Key | Value | Explanation |
|---|---|---|
| cweid | CWE-829 | CWE stands for Common Weakness Enumeration, a list of software weaknesses types. "CWE-829" refers to a specific type of weakness, "Inclusion of Functionality from Untrusted Control Sphere". This generally refers to a situation where a script is pulling in resources from a domain outside of its own, also known as "Cross-Domain JavaScript Source File Inclusion". |
| cvss_score | 6.1 | This represents the base severity score of the vulnerability, following the CVSS v3 (Common Vulnerability Scoring System version 3) framework. It's a decimal number between 0 and 10, where higher values indicate greater severity. In this case, a score of 6.1 indicates a medium-level vulnerability. |
| mitreId | T1170 | This is an identifier from MITRE's ATT&CK framework. "T1170" refers to a specific technique, namely "Dynamic Data Exchange", which is a method of interprocess communication that could potentially be exploited. |
The CVSS v3 base score calculation details what characteristics of the vulnerability led to the score of 6.1. Here's what each piece means:
| Metric | Value | Explanation |
|---|---|---|
| Attack Vector (AV) | Network (N) | This means the attack can be carried out over the network. |
| Attack Complexity (AC) | Low (L) | It's relatively easy to perform the attack. |
| Privileges Required (PR) | None (N) | The attacker doesn't need any specific privileges on the target system. |
| User Interaction (UI) | Required (R) | The attack requires some form of user interaction, such as clicking a link. |
| Scope (S) | Unchanged (U) | The attack does not affect resources beyond the intended target. |
| Confidentiality (C) | Low (L) | If exploited, the attack could slightly compromise the confidentiality of the system's data. |
| Integrity (I) | Low (L) | The attack could slightly compromise the integrity of the system's data. |
| Availability (A) | None (N) | The attack does not affect the availability of the system's data or services. |
Finally, the paragraph at the end explains that although the vulnerability has a medium-level risk, the fact that it isn't exposed to the public internet and that the application is hosted in a secure environment with added controls like network segmentation, access controls, and monitoring makes the associated risk manageable.
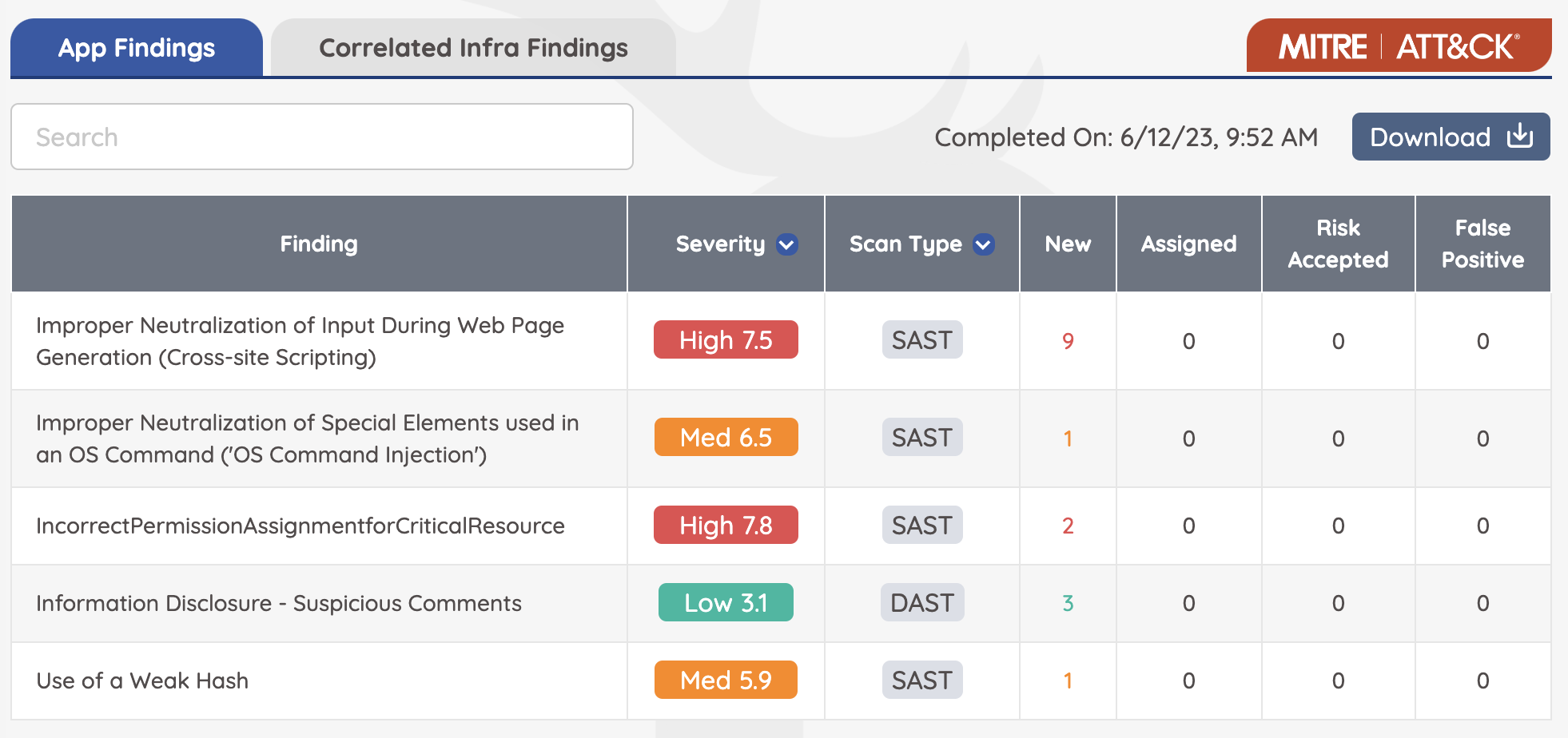
As you can see below, next to each severity level of the vulnerability, the CVSS score is calculated and displayed here