MITRE ATT&CK Framework End-User Documentation
Introduction
The MITRE ATT&CK framework is a comprehensive knowledge base that provides information about tactics, techniques, and procedures (TTPs) used by threat actors during cyber attacks. The framework can be used by organizations to improve their cybersecurity posture by identifying potential weaknesses and developing effective mitigation strategies. This document provides an overview of the MITRE ATT&CK framework and its various components.
Components of the MITRE ATT&CK Framework
The MITRE ATT&CK framework consists of several components, including:
-
Tactic categories: The framework includes 12 tactic categories that describe the various stages of a cyber attack, from initial access to data exfiltration.
-
Techniques: Within each tactic category, there are multiple techniques that describe specific methods used by attackers to achieve their objectives.
-
Sub-techniques: Some techniques have sub-techniques that provide additional granularity and detail about how an attack is carried out.
-
Mitigations: The framework also includes mitigations, which are strategies and techniques that can be used to prevent or reduce the impact of an attack.
Using the MITRE ATT&CK Framework
The MITRE ATT&CK framework can be used by security analysts, incident responders, and other cybersecurity professionals to:
-
Identify potential attack vectors: By understanding the tactics and techniques used by threat actors, organizations can identify potential attack vectors and develop effective mitigation strategies.
-
Develop threat models: The framework can be used to develop threat models that describe the potential risks and vulnerabilities of an organization's systems and infrastructure.
-
Analyze security incidents: Security incidents can be analyzed using the MITRE ATT&CK framework to identify the tactics and techniques used by the attacker and to develop effective response strategies.
-
Select and evaluate security tools: The framework can be used to select and evaluate security tools that are effective at detecting and mitigating specific tactics and techniques.
Integration on Prancer Solution
Prancer's platform can be configured to use MITRE IDs to tag and organize findings or vulnerabilities, allowing users to filter or search for specific vulnerabilities based on the required MITRE IDs or categories.
On PAC Management, find the PAC config file you want your MITRE Attack vulnerabilities, and click on MITRE Attack.
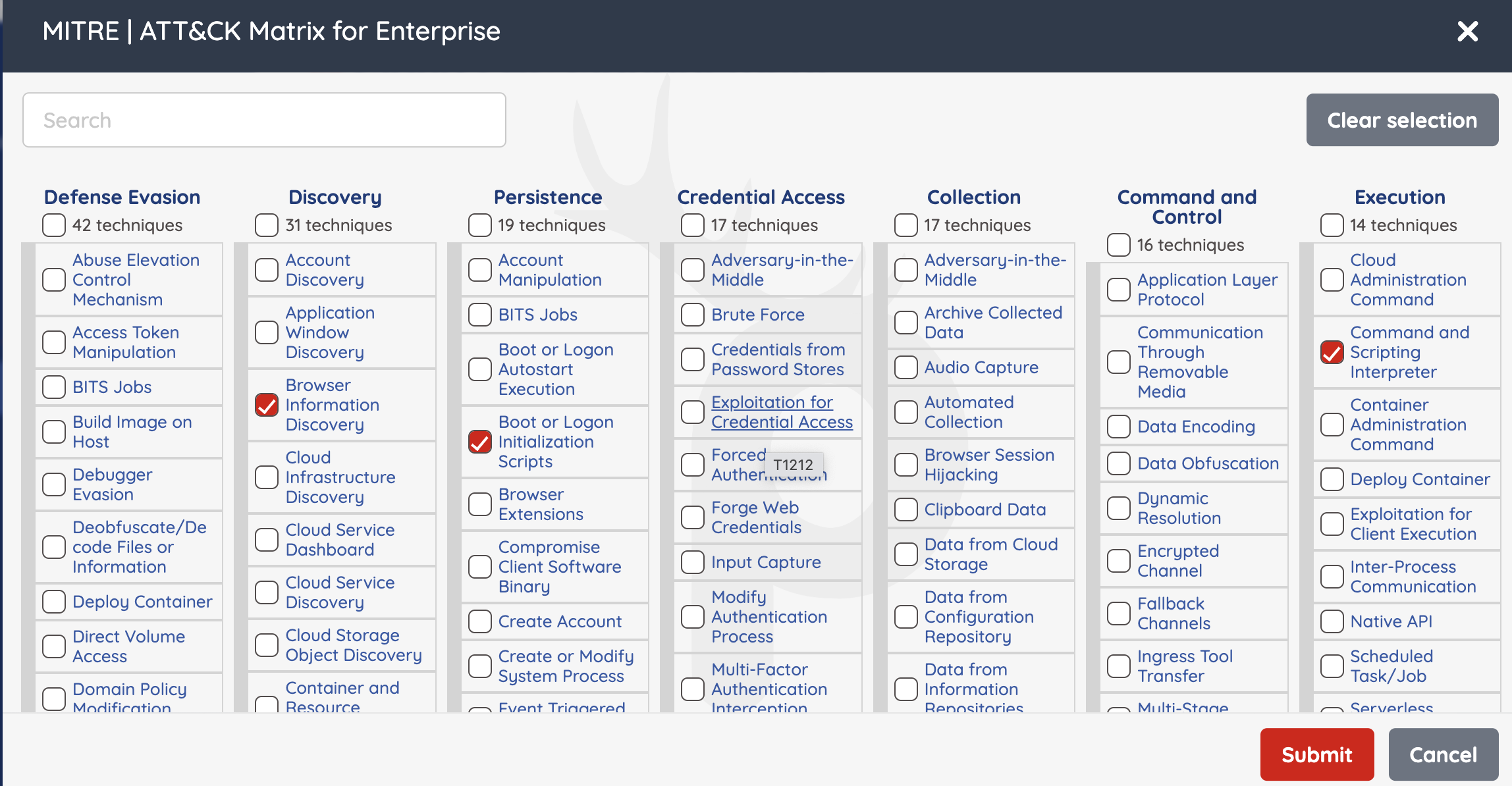
Select the MITRE tags you want to test your application against and click "Submit"
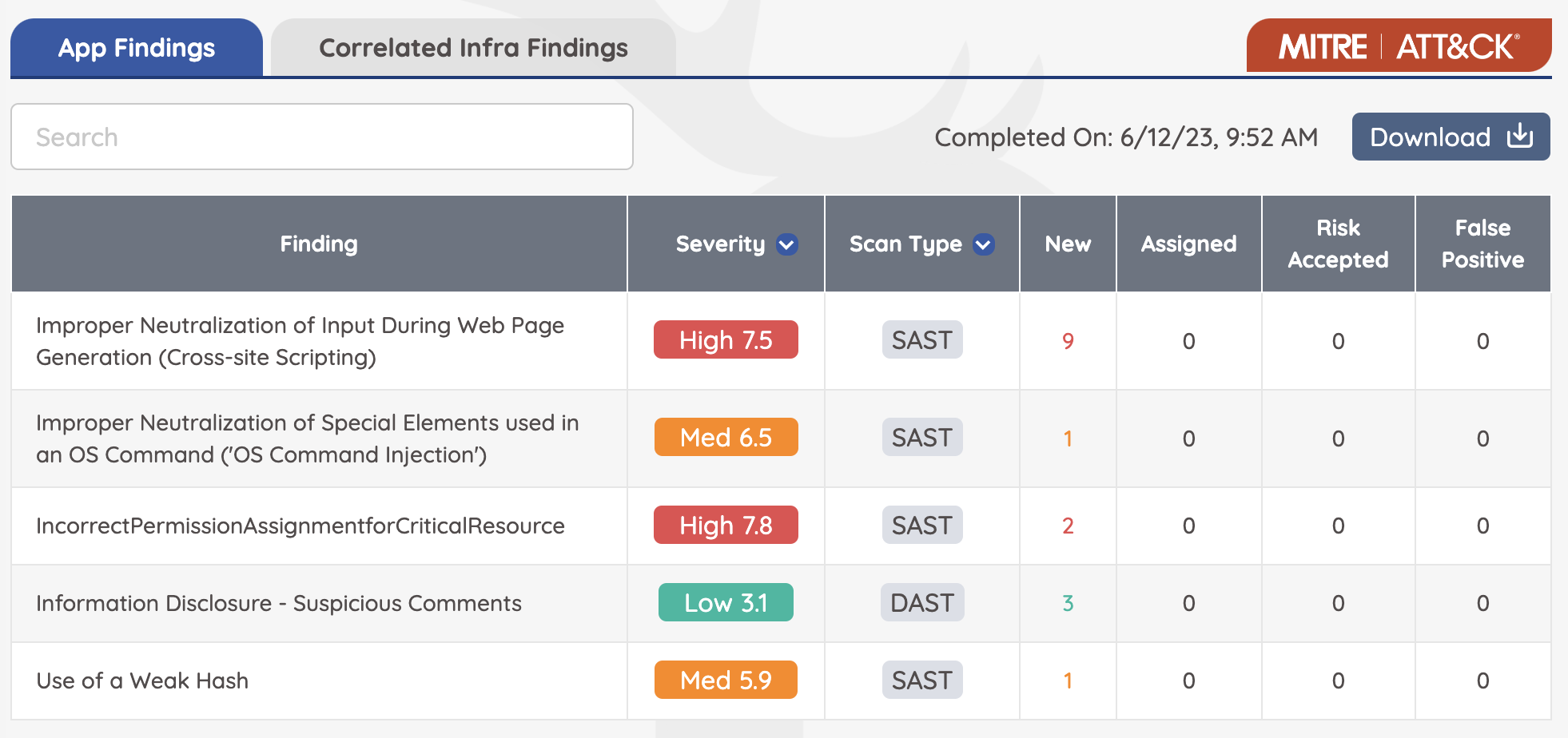
The results will appear like this
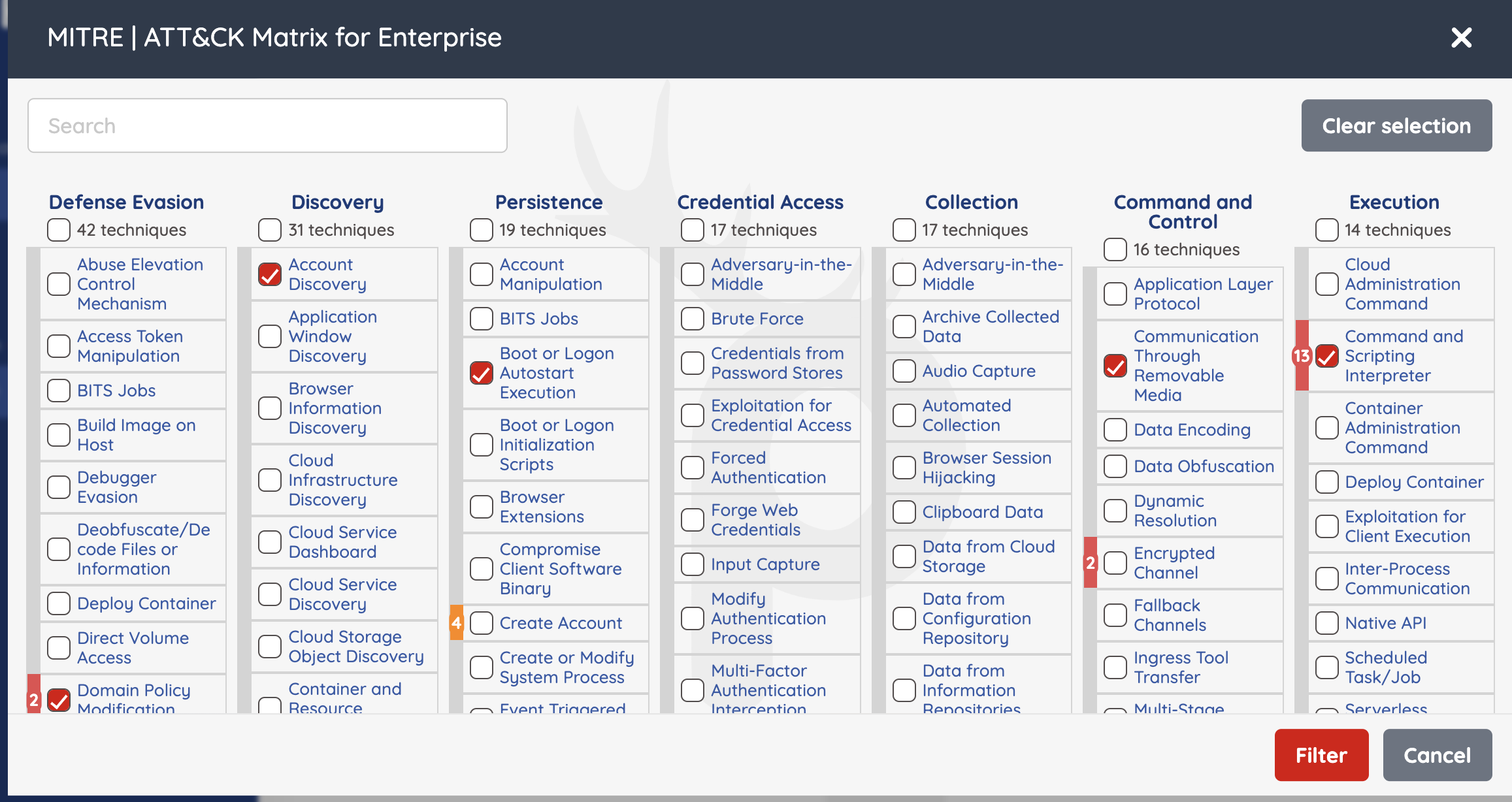
You also have the option to filter your Application findings for specific MITRE Attack vulnerabilities after the pentest is done. From the "App Findings" of the pentest, click on the red "MITRE | ATT&CK" button to filter results
Conclusion
The MITRE ATT&CK framework is a valuable resource for organizations looking to improve their cybersecurity posture. By understanding the tactics and techniques used by threat actors, organizations can develop effective mitigation strategies and better protect their systems and data.