Introduction
It is possible to keep your PAC config file in a remote git repository. This helps you for multiple developers to work on the PAC config files, and also have a git flow to change the content of the PAC file. In this section, we show how to keep PAC configuration files in a remote Git repository for collaboration among multiple developers. To achieve this, a Git connector file needs to be created to connect the Git repository. The connector file specifies the Git provider URL, branch name, and a secret key that will be used to store the Git access token in the Key Vault. Once the connector file is created, it can be uploaded to the PAC management page by drag and drop. To store the authentication token, a new entry needs to be created in the Key Vault with the key name being the value of 'httpsAccessToken' and the key value being the generated access token. The article also provides documentation for creating a personal access token on Github and the necessary permissions that need to be granted.
Create and upload a Git connector file
Needs to create a connector file which will use to connect Git repository.
git_connector.json is the filename being uploaded. The name of the connector will be git_connector and this has to be put in the pac_config as example below:
connector : git_connector
{
"branchName": "<<Branch Name>>",
"companyName": "<<Company Name>>",
"fileType": "structure",
"gitProvider": "<<full github link eg.https://github.com/prancer-io/prancer-pac-sample.git>>",
"httpsAccessToken": "<<Key Vault Key Name| We will store key vault value post this file is created eg. secret-git-key >>",
"private": true,
"type": "filesystem"
}
Name of the collection defined in git
| Field | Value | Description |
|---|---|---|
| gitProvider | clone URL | The URL for clone the git repository. |
| branchName | branch name | Git branch name where the zap scripts are available |
| httpsAccessToken | secret key | Any secret key which will be used to store the git token in the key vault |
Guidelines for Generating Secret Keys from Git Providers
| Git Provider | Required Permissions |
|---|---|
| GitHub | Scopes needed: repo, user |
| GitLab | Scopes needed: read_api, read_user, read_repository |
| Bitbucket | Scope needed: Repositories -> Read |
- Once the connector file is created then Drag and drop the file over a collection in PAC anagement page.
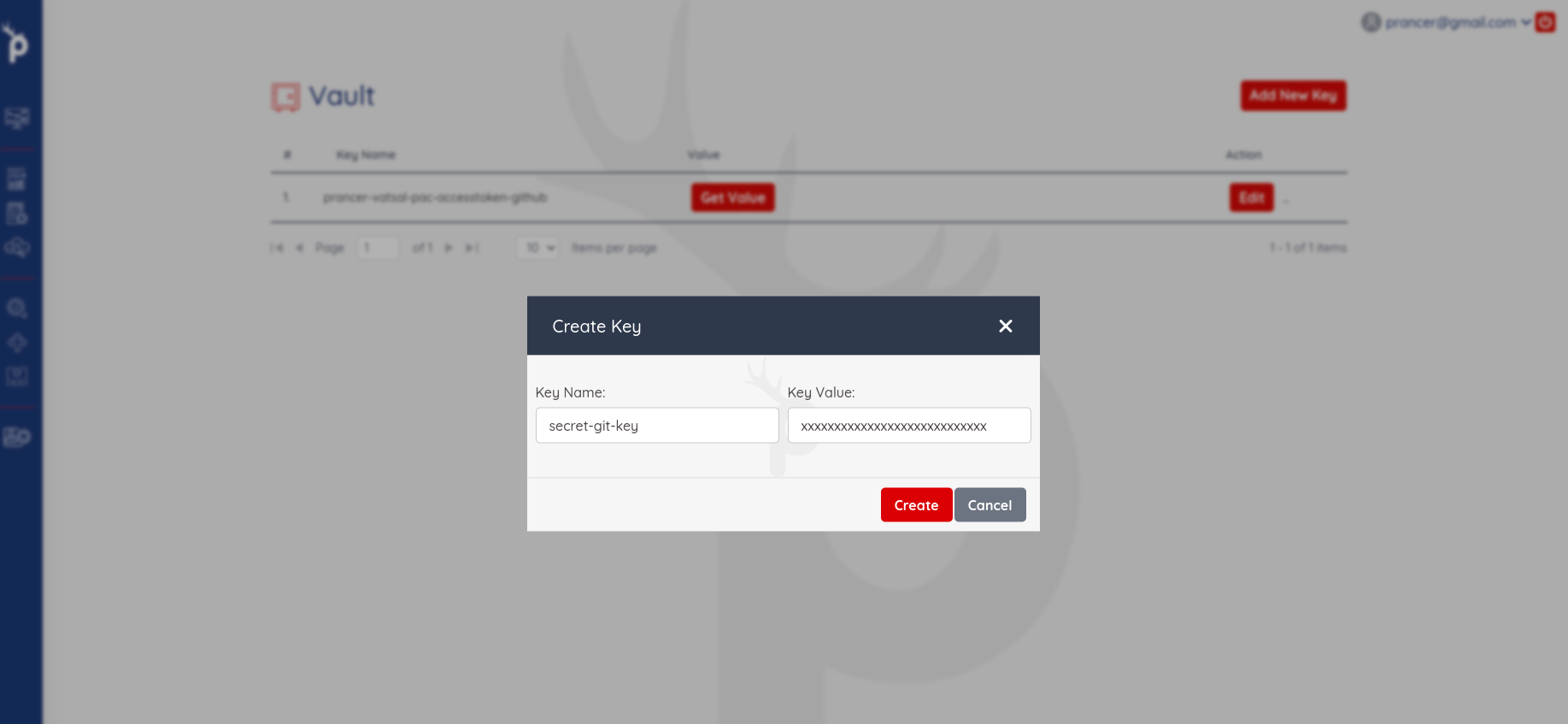
Store the secrets in Key Vault
Required to store the authentication token to connect and clone the Git repository. Generate the git access token from the Git console. Here is the documentation for create the personal access token on Github.
- Give the following permissions while generating the access token.
repo: Full control of private repositories
project: Full control of projects
read: user Read ALL user profile data
Create the new entry in Key Vault, where Key Name is the value of httpsAccessToken and Key Value is generated access token.