Loading Attacks Based on Auto Tagging
When running a pentest on Prancer PAC solution, if we want to do a pentest based on Custom addons, we would have to enter in CVE details, which contains the path about where the addons are stored and which ones to test against. Custom addons
This documentation talks about the same process. However, instead of manually enter CVE details, we have the option to configure tags in the file our addons are located at, and in the PAC Config file, we can test the addons by entering the configured tags.
** Prerequisites **
-
Have custom addons codified and stored in Github Repository
-
metadata.yaml file
metadata.yaml file
In Github, the branch in which the addons are located contains a metadata.yaml file.
At the bottom of that metadata.yaml file, create and label your tags as to how you want to load your custom addons. Here is an example of a metadata.yaml file with tags:-
Name:
Type: addon
Engine: java
Description:
Charset: UTF-8
tags:
cloud: azure,aws,gcp,custom
language: java
Now that we have the tags configured in metadata.yaml file, we can go ahead and load these configured tags on our PAC Config file. Here is an example of a PAC Config file that executes this process.
Collection: test_aws
ConnectionName: test_aws_connector
CloudType: aws
ApplicatioName: AutoTagValidation_AV
RiskLevel: attack
Compliance:
- CIS
ApplicationType: WebScan
Schedule: onetime
Target: https://javavulny.prancer.cloud
Tags:
cloud: azure
language: java
WebScan:
AjaxSpider: false
Scanner:
Cloud:
Platform:
AWS:
AfterRun: delete
EcsExecRoleArn: ""
NewFargate:
External:
AccountId: "135633075302"
Region: us-west-2
TaskDefinition: pentest-task
ClusterName: pentest-cluster
SecurityGroup: pentest-security-group
ContainerName: prancer-scanner
SubnetId: subnet-0b4616868d91c854c
VpcCidr: ""
SubnetCidr: ""
IGCidr: ""
TokenSecretsManagerArn: ""
AuthenticationMethod: noAuthentication
# All the addons ID listed on link https://www.zaproxy.org/addons.
AddOns:
# - accessControl
# - ascanrulesAlpha
In this file, we see that the tag has been configured. In the metadata.yaml, we configured all cloud environments our solution supports. Nonetheless, we don't need all 4 cloud in the Tags section of PAC Config file.
Tags:
cloud: azure
language: java
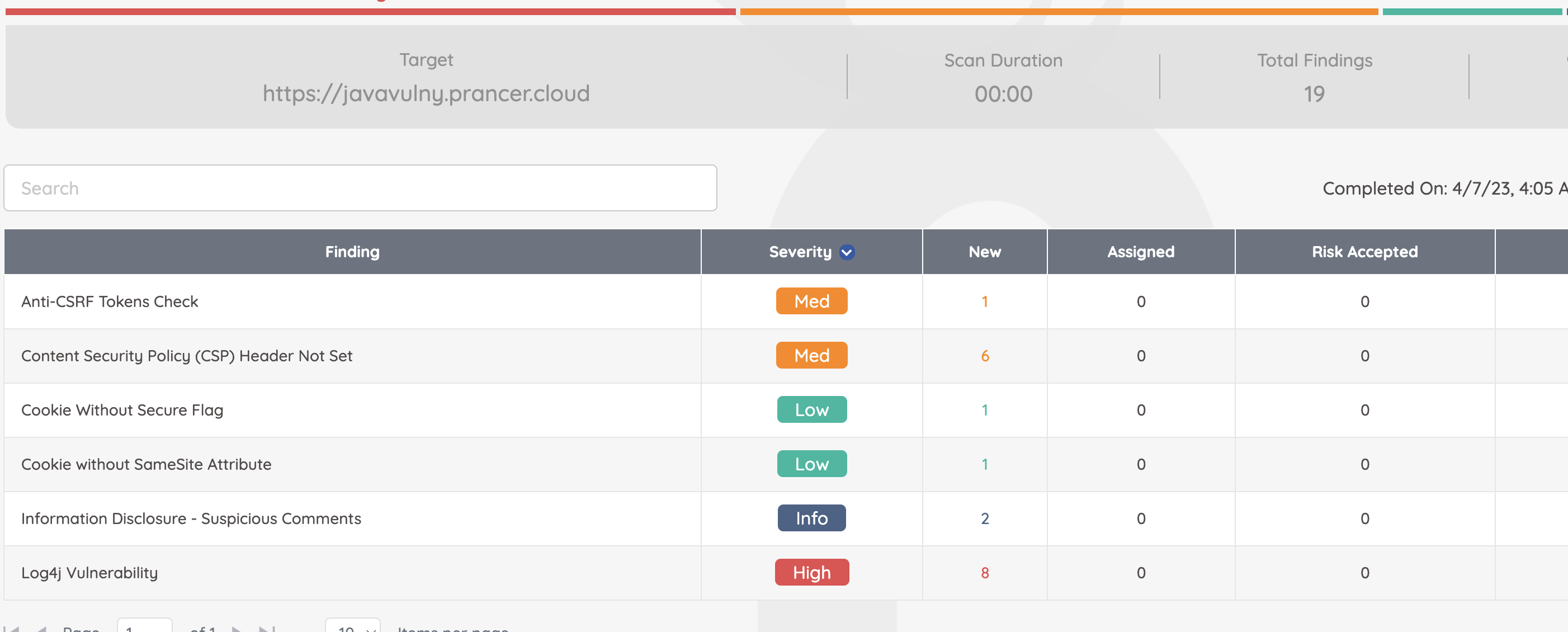
Now, we run the PAC Config file, and without adding any details about where the files are located on Github, without specifying and Git path details, here are the results that are generated just by entering the tags that were configured in the metadata.yaml file for the addons that needs to be tested:-