AWS Cloud Template (Cloud Formation)
Some companies have internal or regulatory compliance to follow certain rules to create resources in their cloud environment. Because of that, we are providing a feature to create cloud resources based on the IaC template in the cloud.
Cloud Formation
AWS CloudFormation allow clients to create resources like TaskDefintion,Cluster,SecurityGroup,EC2, S3, VPC, ELB etc using JSON|YAML based template file, which comes under Cloud Formation.Cloud Formation is basically AWS template based platform which make our life easy for creating and deleting resources on AWS Platform.
Prancer Pentesting for Web application using Cloud formation
Create PAC Config, which is helpful to create AWS Resource by using Cloud Formation Template And it will help to run Pentest for provided target machine.
Pre-requisites
- Create Github Repository private/public
- Generate new/Existing Github AccessKey, with permission to Clone the project
- Cloud Formation Template must be added just like this sample template, Note it should have replaced with parameters.
- Family under the MyTaskDefinition.
- ExecutionRoleArn under the MyTaskDefinition.
- TaskRoleArn under the MyTaskDefinition.
- Name under the ContainerDefinitions.
- Image under the ContainerDefinitions,
- ClusterName under the ECSCluster.
- GroupDescription under the EcsSecurityGroup.
Note: For Container Image have following examples - prancer/prancer-pac. ===> always refer to hub.docker.com:prancer/prancer-pac:latest
- public.ecr.aws/u4p5w7f1/prancer-pac:latest. =====> this refers to amazon;s current account's public repository and this will pulled and the penetration test will run from this image
Create PAC Config using following Steps
Create Git Connector using following Steps
Update the PAC Config file:
- Open the PAC Management screen and click on PAC Configuration for which you want to add the script.
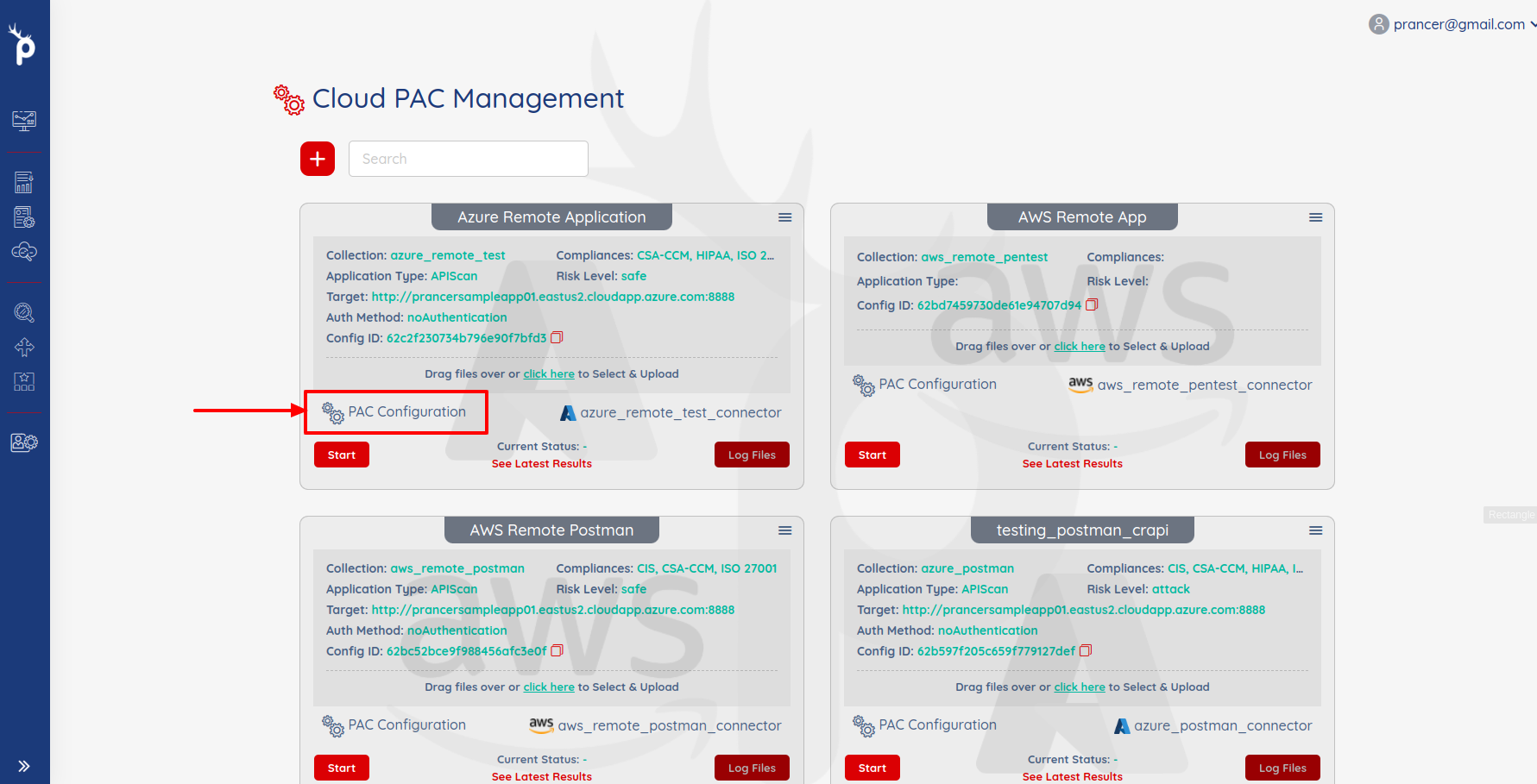
Add the AWS field in the PAC configuration file.
Scanner:
Cloud:
Platform:
AWS:
Connector: <<git-connector>>
StackName: <<name-of-stack>>
TemplateFile: <<git location for template file eg. /cloud-formation/existing/ecs-template.json >>
ParamsFile: <<git location for params file eg. /cloud-formation/existing/ecs-params.json >>
| Field | Value | Description |
|---|---|---|
| Connector* | connector name | the Connector value would be the git connector file name. |
| TemplateFile* | template path | Provide location on Git repository must have cloud Formation template located. |
| ParamsFile | params path | Provide location on Git repository must have cloud Formation params file located. |
You can find Complete PAC File like this
Collection: aws
ConnectionName: aws_connector
CloudType: aws
ApplicatioName: template_safe_001
RiskLevel: safe
Compliance:
- CIS
- HIPAA
ApplicationType: WebScan
Schedule: onetime
Target: <<your target endpoint>>
Scanner:
Cloud:
Platform:
AWS:
AfterRun: delete
Connector: github_connector_collection
TemplateFile: /cloud-formation/existing/ecs-template.json
StackName: prancer-external-scanner
NewFargate:
External:
AccountId: "<<account Id>>"
Region: us-west-2
TaskDefinition: pentest-task
ClusterName: pentest-cluster
SecurityGroup: pentest-security-group
ContainerName: prancer-scanner
SubnetId: <<subnet Id>>
AuthenticationMethod: noAuthentication
AddOns:
- accessControl
- ascanrulesBeta
- sqliplugin
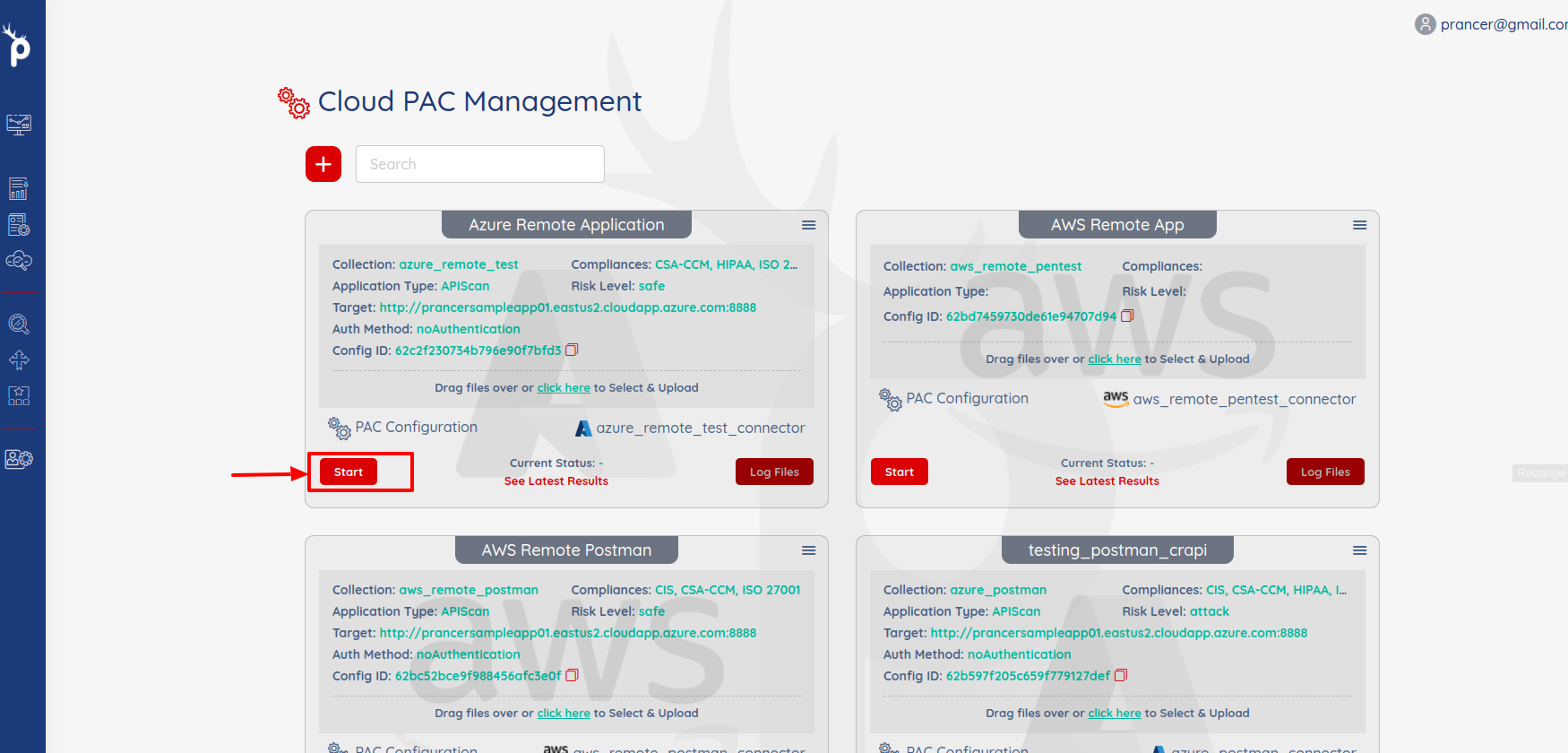
Run the Pentest:
- Click on
startbutton to run the pentest.
- After sometimes when the Pentest will complete then you can see the results by click on
See Latest Resultslink.
- It will open the
Application Security Findingspage.