PAC JWT AUTHENTICATION
Overview
This document discusses the use of JWT-based authentication for authenticated pentesting using Prancer. JWT-based authentication is an alternative to traditional password-based authentication, using asymmetric (public-key) cryptography to register, authenticate and perform second-factor authentication with websites. This method has several benefits, including protection against phishing and reduced impact of data breaches. To set up JWT-based authentication in Prancer, the user needs to go through a series of steps in the PAC wizard page and enter details such as the key vault, login URL, and login body template. The PAC file also includes additional fields such as the Login Indicator, Authorization Type, Authorization Key and Authorization Token Type.
Authentication
The Web Authentication API (also referred to as WebAuthn) uses asymmetric (public-key) instead of passwords or SMS texts for registering, authenticating, and second-factor authentication with websites. This has some benefits:
Protection against phishing: An attacker who creates a fake login website can't login as the user because the signature changes with the origin of the website. Reduced impact of data breaches: Developers don't need to hash the public key, and if an attacker gets access to the public key used to verify the authentication, it can't authenticate because it needs the private key. Invulnerable to password attacks: Some users might reuse passwords, and an attacker may obtain the user's password for another website (e.g. via a data breach). Also, text passwords are much easier to brute-force than a digital signature.
Prancer authenticated pentesting
Prancer tries to support different authentication methods such as formbase,jwt,cookie,oauth and etc. As all applications have authentication to scan all paths, prancer pentest scanner should be authenticated to send request to the APIs and pages that are behind the auth-middleware.
For setting up authentication we need to create scanner at first. here are some steps which is required to be setup before auth configuration.
- go to pac wizard page
- select cloud type
- select collection and connector (scanner will be created in the resources which the selected connector has an access)
- put application information
- select existing or new instance to run the pentest
- define target domain or select from existing resources
In this step you should be able to see authentication page.
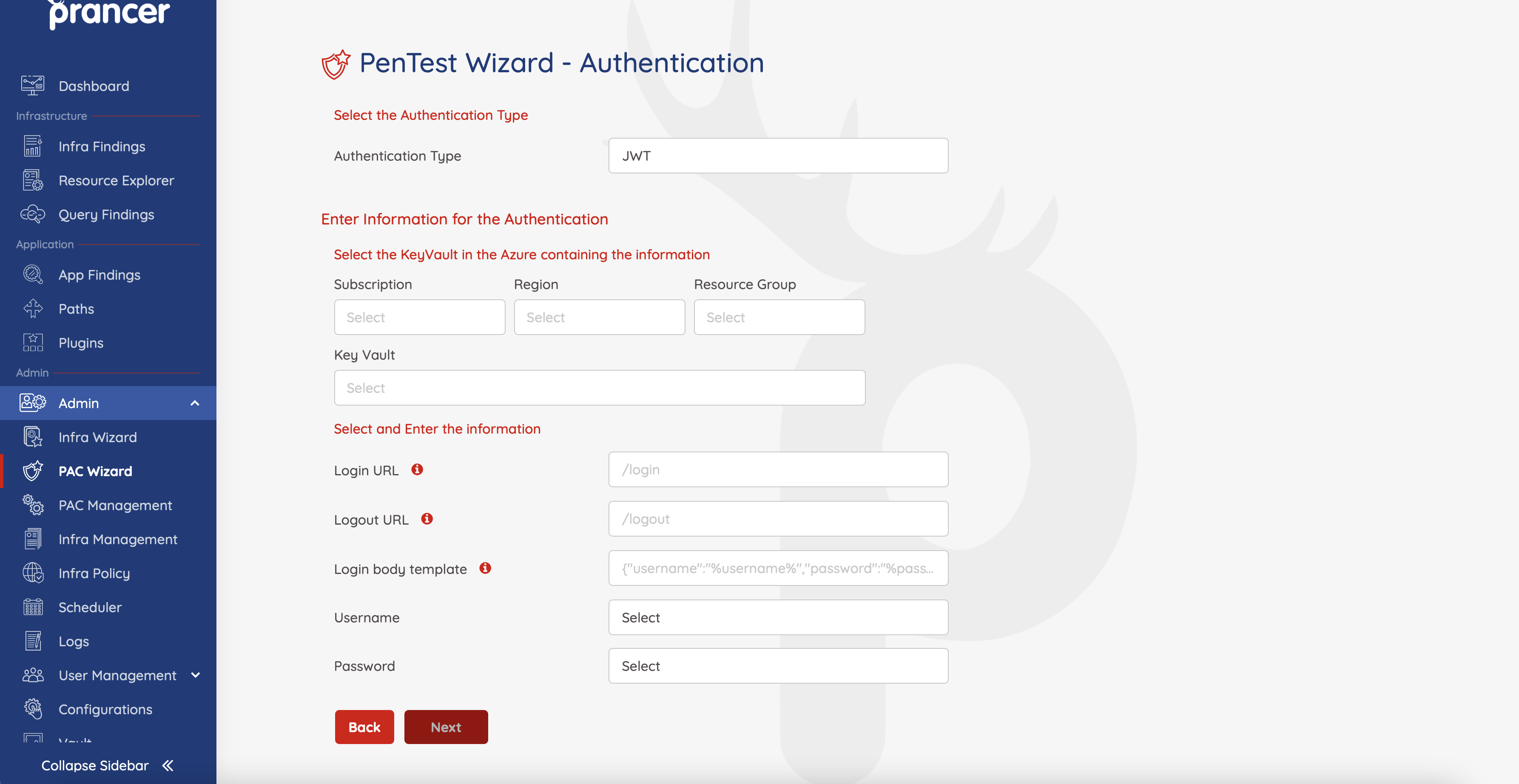
In this page we have different parameters. Here is some explanation for each field:
| Field | Available values | Description |
|---|---|---|
| Authentication Type | FromBase,JWT,Cookie,Oauth,Custom | In this field we should select what is our authentication type |
| Key Vault | every key Vault which the connector has access to it | we're going to choose key Vault for selecting secrets like user name and password or etc. |
| Login URL | ex: https://sample.com/login | In this field should put complete url for login, by this field scanner will be able to find where should login request send to. |
| Logout URL | ex: https://sample.com/logout | In this field you should put logout url, this field will be exclude from URLs to prevent logging out the scanner user |
| Login body template | ex: {"username":"%username%","password":"%password%"} | This field will help scanner to find out which format is valid format for sending request to login url |
| username | select password from keyvault secrets | after we choose keyvault or secret manager we need to select username and password. These variables should be select from the keyvault or secret manager secrets |
| password | select password from keyvault secrets | after we choose keyvault or secret manager we need to select username and password. These variables should be select from the keyvault or secret manager secrets |
complete page can be like below.
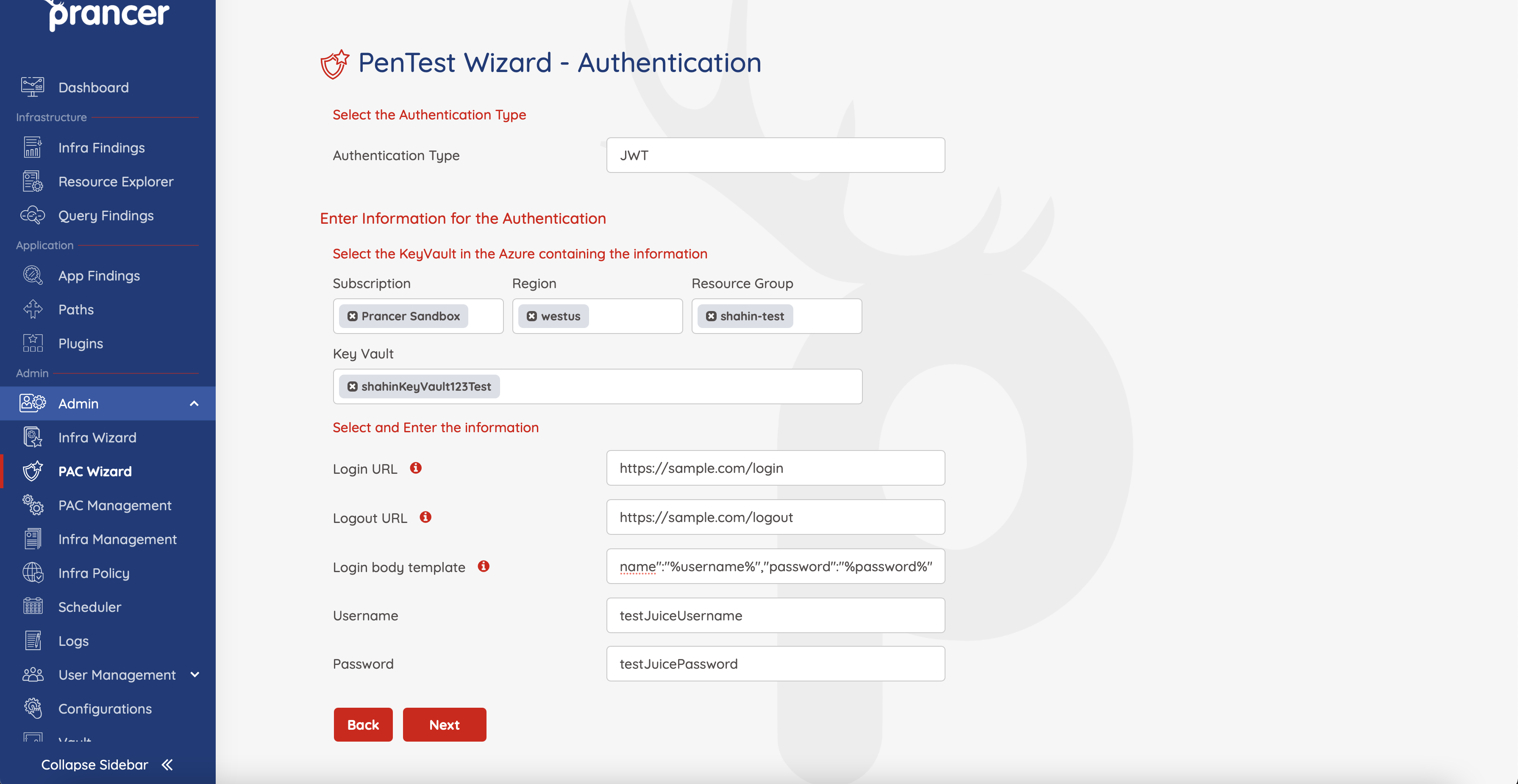
You can find completed pac file in below
Collection: shahin_test
ConnectionName: shahin_test_connector
CloudType: azure
ApplicatioName: sample application
RiskLevel: safe
Compliance:
- CIS
ApplicationType: WebScan
Schedule: onetime
Target: https://samople.com
Scanner:
Cloud:
Platform:
Azure:
ContainerInstance:
AfterRun: delete
NewContainerInstance:
External:
SubscriptionId: a6941677-4c37-42fb-960c-dad8f25060a3
ResourceGp: pac
Region: eastus
ContainerGroupName: prancer-scanner-group
ContainerName: prancer-pentest-instance
ResourceName: prancer-instances
AuthenticationMethod: jwtAuthentication
Authentication:
JWTAuth:
UsernameSecretKey: testJuiceUsername
PasswordSecretKey: testJuicePassword
LoginUrl: https://sample.com/login
LogoutUrl: https://sample.com/logout
LoginBodyTemplate: '{"username":"%username%","password":"%password%"}'
LoginIndicator: ^.*token.*$
AuthorizationType: Header
AuthorizationKey: Authorization
AuthorizationTokenType: Bearer
Vault:
Azure:
KeyVaultName: shahinKeyVault123Test
SubscriptionID: a6941677-4c37-42fb-960c-dad8f25060a3
Region: westus
ResourceGp: shahin-test
# All the addons ID listed on link https://www.zaproxy.org/addons.
AddOns:
# - accessControl
# - ascanrulesAlpha
As you understand we have some fields in pac file which is not exist in the wizard. Lets focus on them :
| Field | Available values | Description |
|---|---|---|
| LoginIndicator | regex string | After scanner send request to authentication URL, it will get response and find out if loginIndicator regex compile is success or failed. If success scanner will be understand that authentication was success and it will extract token from authentication response. |
| AuthorizationType | Header,Body | This field will add all authenticated params in header if the value of this is header |
| AuthorizationKey | ex : Authorization | any header name can be put as Authorization key , this field is related to the name which we should set for authentication params in header |
| AuthorizationTokenType | ex: Bearer | This field is prefix which scanner will set before token value in header. It can be empty sting too |
Note: LoginIndicator value in the PAC file can be regex or the actual parameter path. e.x. If the response containing the JWT token looks like the following json response, then the LoginIndicator value can be "body.token"
{body: {
id: 1,
token: JWT token value,
}}