Pentest with Postman Collection
Introduction
This page explains how to use Postman collections to create a PAC configuration that can be used to conduct API pentesting using Prancer. It requires the creation of a GitHub repository and a new/existing GitHub access key. The Postman collection file to be tested must be added to the created repository. The configuration file must be updated by adding the APIScan field and configuring its fields with the relevant values, such as OpenAPI type and git direction provider. Once the configuration file is completed, the pentest can be run by clicking the start button on the PAC management screen. After completion of the pentest, the results can be viewed on the application security findings page.
Many developers use Postman to develop and test their APIs. PAC provides a feature to load all the API endpoints from Postman collections and use them to pentest the API application. The following tutorial will help you to create PAC Config, which is helpful to setup Open API to do Pentest for provided target machine and for provided API's in the OpenAPI file.
Prancer also supports using OpenAPI Specification to develop and test API functionality. PAC provides feature to test all endpoints from OpenAPI specification file (json or yaml).
The sections also provide ways to use either of the modes to test APIs.
Pre-requisite
1) Create Github Repository private/public.
2) Generate new/Existing Github AccessKey, with several permission i.e clone project.
3) Postman Collection File to be added in above created Repo eg for sample.
4) OpenAPI specification File to be added in above created Repo eg for sample.
-
Create PAC Config using following Steps
-
Create and upload a Git connector file using following Steps
Update the PAC Config file:
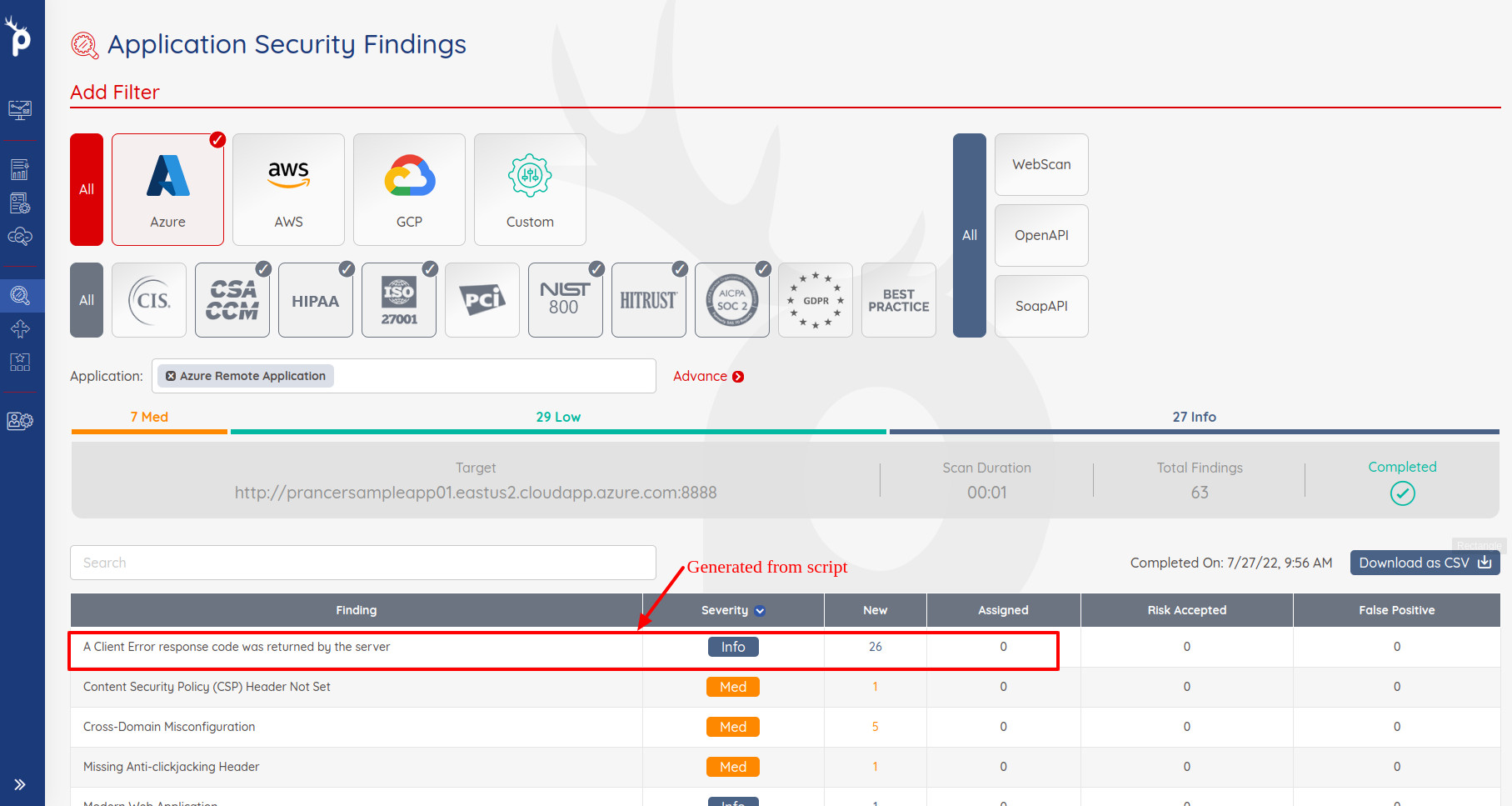
- Open the PAC Management screen and click on PAC Configuration for which you want to add the script.
Add the APIScan field in the PAC configuration file.
Scenario 1 - API configuration files either Postman or Swagger in a repository.
APIScan:
Type: OpenAPI <----- It Must be OpenAPI
DirectionProvider: git <----- It must be git
Direction: <----- It can be empty
SwaggerFile: <----- It can be empty. If not empty this will be first priority. eg. vampi-swagger/openapi3.yaml
Connector: <<git-connector>>
PostmanRemoteFile: <<git location for template file eg. remote_postman/postman_collection.json>>
PostmanEnvRemoteFile: <<git location for template file eg. remote_postman/postman_environment.json>>
Scenario 2 - API configuration files for Postman in a repository.
APIScan:
Type: OpenAPI <----- It Must be OpenAPI
DirectionProvider: git <----- It must be git
Direction: <----- It can be empty
SwaggerFile: <----- It should be empty. If not empty this will be first priority.
Connector: <<git-connector>>
PostmanRemoteFile: <<git location for template file eg. remote_postman/postman_collection.json>>
PostmanEnvRemoteFile: <<git location for template file eg. remote_postman/postman_environment.json>>
Scenario 3 - API configuration files either Postman or Swagger in a URL. Swagger is given higher priority when both are present.
APIScan:
Type: OpenAPI <----- It Must be OpenAPI
DirectionProvider: link <----- It must be link
Direction: <----- It can be empty
SwaggerFile: <<eg. https://raw.githubusercontent.com/prancer-io/prancer-pac-sample/refs/heads/main/vampi-swagger/openapi3.yaml>>
Connector: <----- It should be empty
PostmanRemoteFile: <<eg: https://raw.githubusercontent.com/prancer-io/prancer-pac-sample/refs/heads/main/vampi-postman/vampi_collection.json>>
PostmanEnvRemoteFile: <<eg: https://raw.githubusercontent.com/prancer-io/prancer-pac-sample/refs/heads/main/vampi-postman/vampi_environment.json>>
Scenario 4 - API configuration files for Postman in a URL. Swagger is given higher priority when both are present.
APIScan:
Type: OpenAPI <----- It Must be OpenAPI
DirectionProvider: link <----- It must be link
Direction: <----- It can be empty
SwaggerFile: <----- It should be empty. If not empty this will be first priority.
Connector: <----- It should be empty
PostmanRemoteFile: <<eg: https://raw.githubusercontent.com/prancer-io/prancer-pac-sample/refs/heads/main/vampi-postman/vampi_collection.json>>
PostmanEnvRemoteFile: <<eg: https://raw.githubusercontent.com/prancer-io/prancer-pac-sample/refs/heads/main/vampi-postman/vampi_environment.json>>
| Field | Value | Description |
|---|---|---|
| Type* | Type of Direction | The Type contains either OpenAPI |
| DirectionProvider* | Open API Direction Provider | The Direction Provider contains either git |
| Connector* | connector name | the Connector name would be file name of git connector. |
| PostmanRemoteFile* | template path | Provide Postman collection location(only JSON format) in a URL or a Git repository path. |
| PostmanEnvRemoteFile | params path | Provide Postman Environment(only JSON format) in a URL or a Git repository path. |
| Direction* | OpenAPI path | Provide OpenAPI file in a URL or a Git repository path. |
| SwaggerFile* | OpenAPI path | Provide OpenAPI file(JSON or YAML extension) in a URL or a Git repository path. |
The URLs in the above list should be accessible from the location of running the PAC scanner.
You can find Complete PAC File like this
Collection: aws_connection
ConnectionName: aws_connection_connector
CloudType: aws
ApplicatioName: postman_open_api
RiskLevel: safe
Compliance:
- CIS
- HIPAA
ApplicationType: APIScan
Schedule: onetime
Target: <<Target End Point >>
# You can use postman collection as code for running attack inside the prancer.
# PostmanCollectionRepo can include the repository of the postman collection.
# Postman remote files should include a path which has postman collection file and
# for postman env remote files, if you have environment variable file you can put
# the path inside the postmanEnvRemote file so prancer will go and extract the env
# variables and their values and merged it with postman collection.
APIScan:
Type: OpenAPI
DirectionProvider: git
Direction: ""
SwaggerFile: ""
Connector: git_connector
PostmanRemoteFile: postman-convertor/crAPI Accepted.postman_collection.json
PostmanEnvRemoteFile: postman-convertor/Crapi.postman_environment.json
paths:
exclude: []
include: []
Scanner:
Cloud:
Platform:
AWS:
AfterRun: delete
NewFargate:
External:
AccountId: "<<Account Id >>"
Region: us-west-2
TaskDefinition: pentest-task
ClusterName: pentest-cluster
SecurityGroup: pentest-security-group
ContainerName: prancer-scanner
SubnetId: <<Subnet ID >>
AuthenticationMethod: jwtAuthentication
Authentication:
JWTAuth:
UsernameSecretKey: crUsername
PasswordSecretKey: crPassword
LoginUrl: /identity/api/auth/login
LogoutUrl: /identity/api/auth/logout
LoginBodyTemplate: '{"email":"%username%","password":"%password%"}'
LoginIndicator: ^.*token.*$
AuthorizationType: Header
AuthorizationKey: Authorization
AuthorizationTokenType: Bearer
Vault:
Aws:
SecretManager: arn:aws:secretsmanager:us-west-2:<account-id>:secret:<name>
Region: us-west-2
AccountId: "<<account-id>>"
# All the addons ID listed on link https://www.zaproxy.org/addons.
AddOns:
# - accessControl
# - ascanrulesAlpha
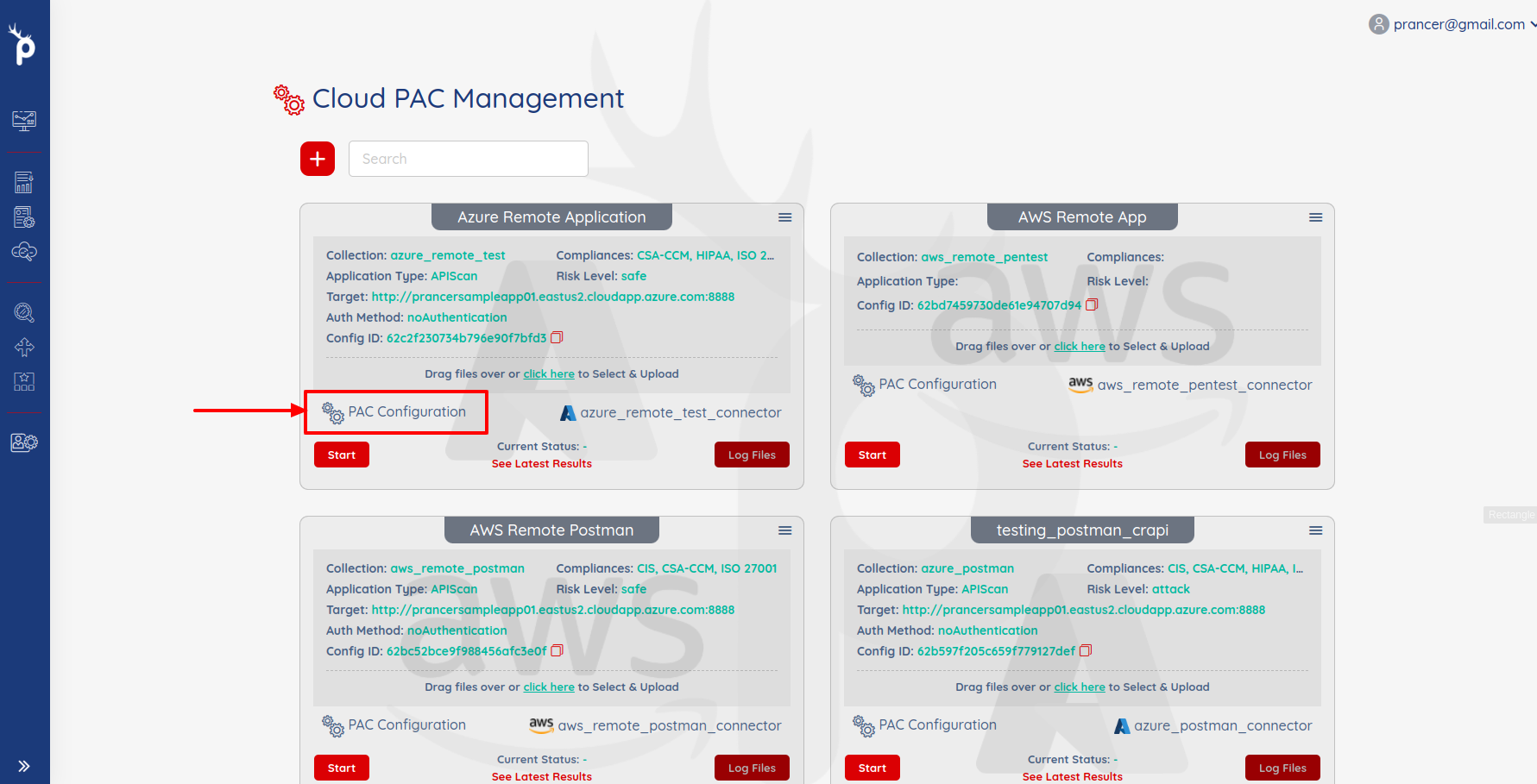
Run the Pentest:
- Click on
startbutton to run the pentest.
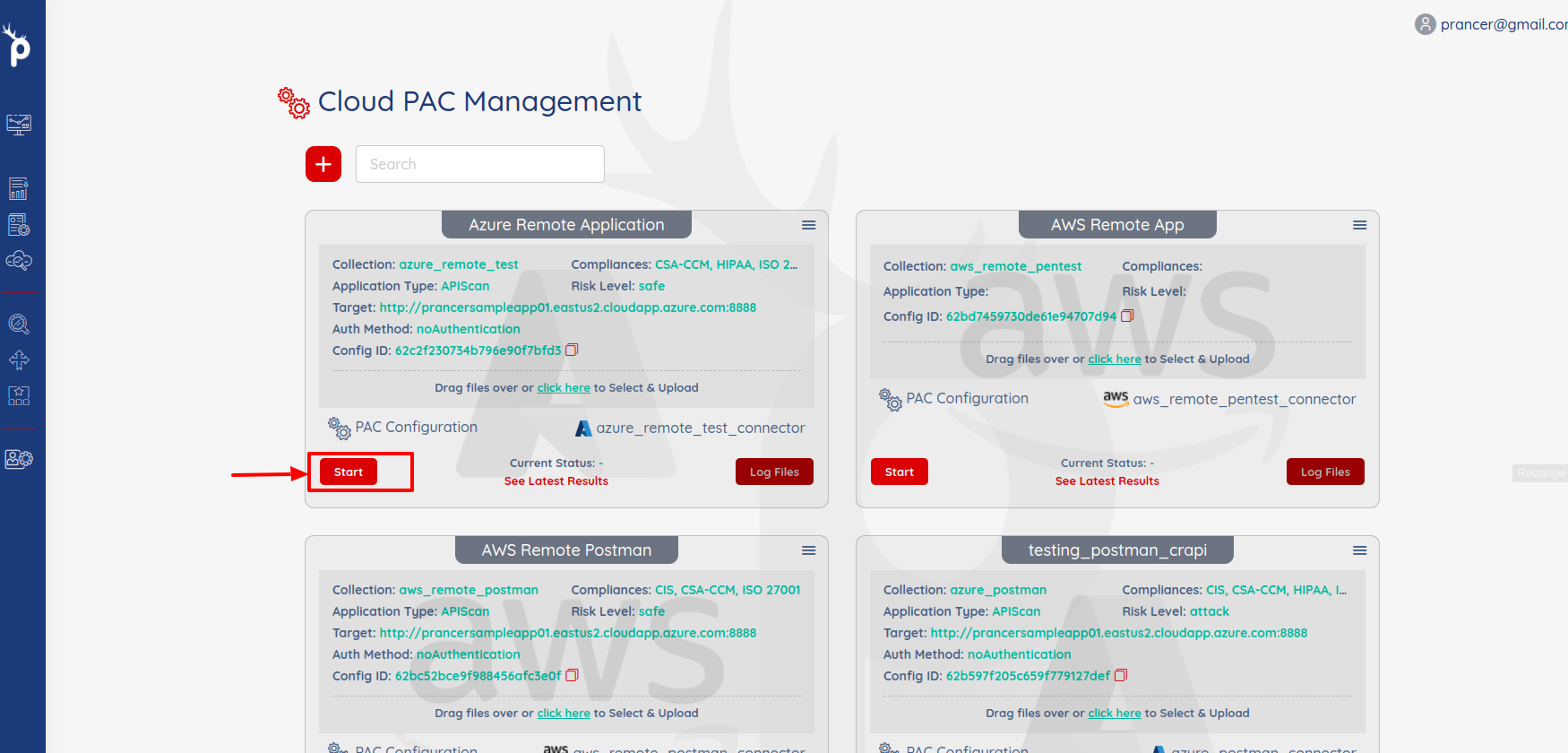
- After sometimes when the Pentest will complete then you can see the results by click on
See Latest Resultslink.
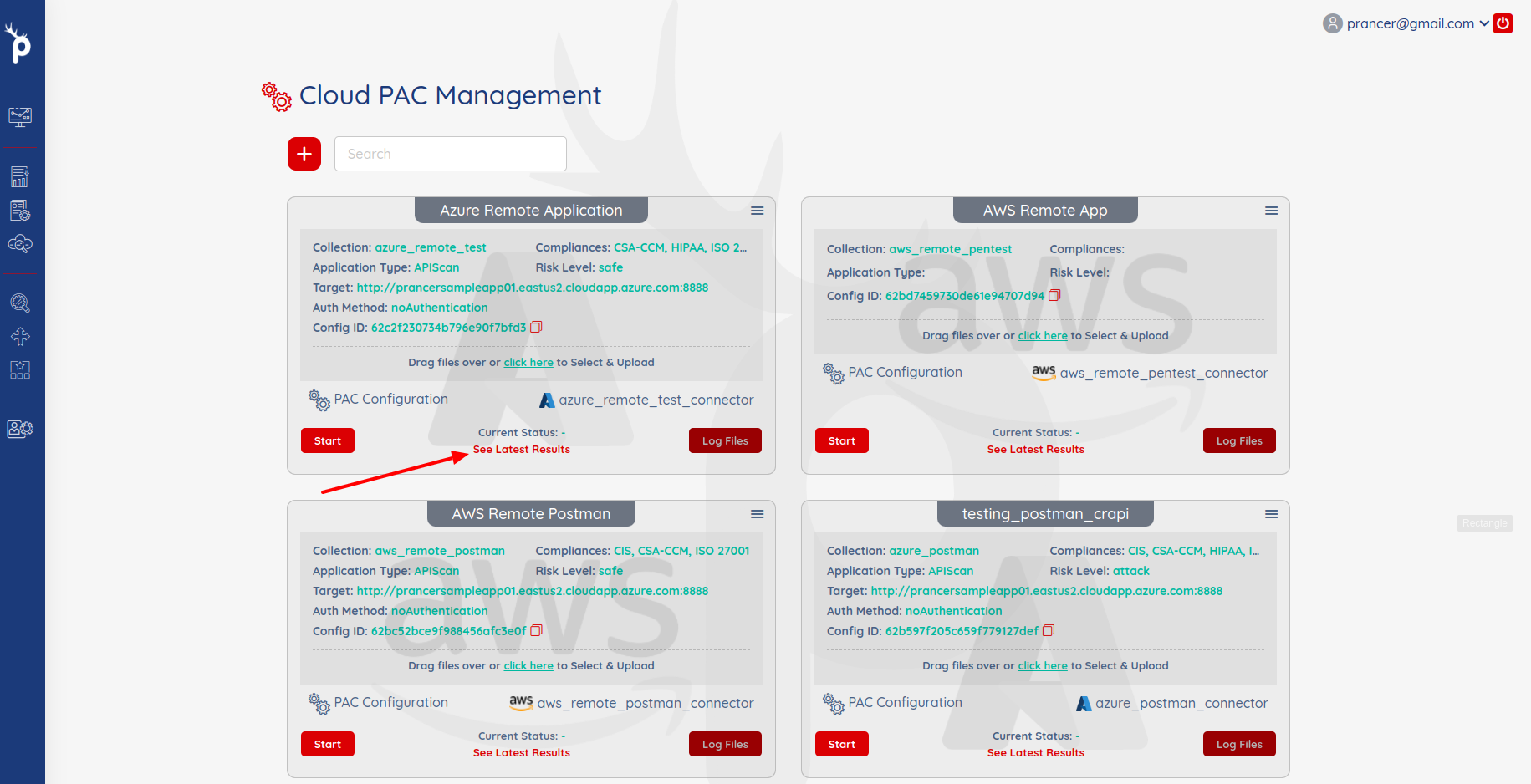
- It will open the
Application Security Findingspage.