Wizard - IaC Scan for Github Enterprise Server - Non internet routable
Introduction
Github Enterprise Server is a virtual appliance from GitHub installed on the company's private network. Suppose the GitHub Enterprise Server is only available within the intranet (non-internet routable). In that case, we need to run prancer CLI within the company's network and send the results back to the Prancer SaaS solution.
This walkthrough applied to the following scenario: - GitHub Enterprise Server containing the code repos - GitHub Enterprise Server is not reachable from the internet
Collection Creation
- Go to Prancer Portal
- from the sidebar select
configuration wizardto create a new collection
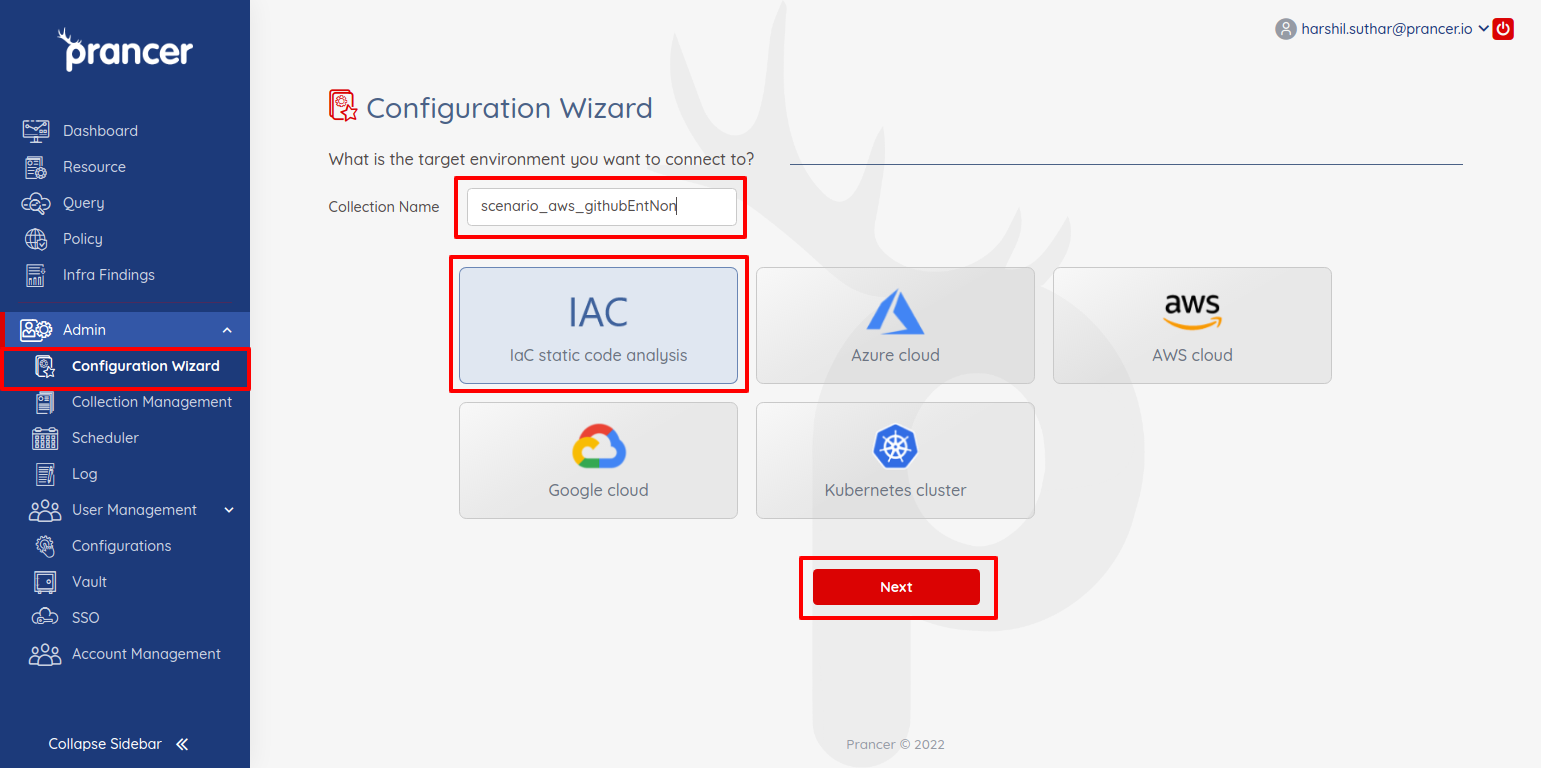
- Provide a name of the collection and select IAC type and click next for next configurations.
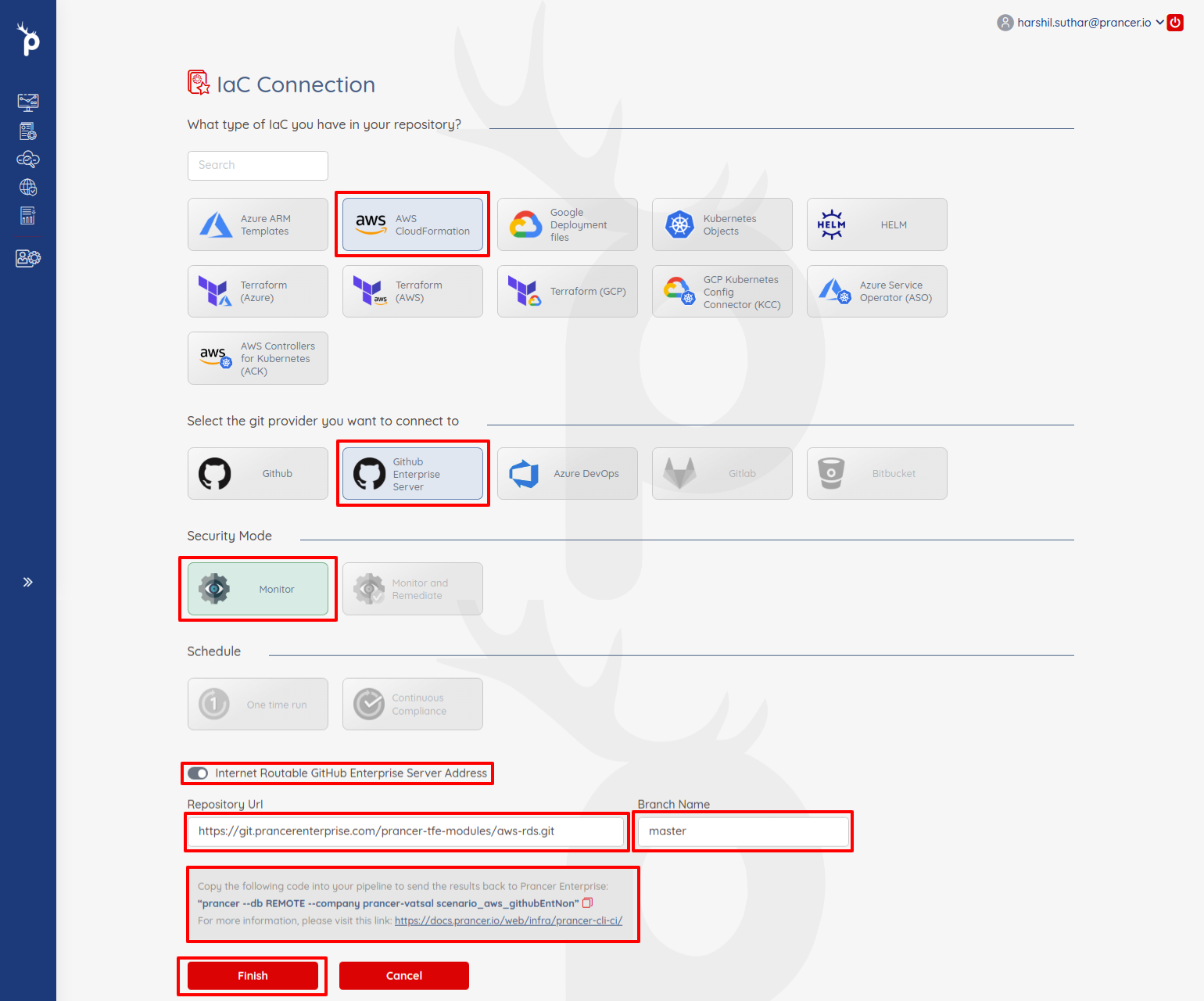
- Select the type of the collection from items like
aws cloudformation,aws terraform,Azure Arm templatesetc. - Select
Github Enterprisefrom the git provider section - There will be only monitor mode will be available for non internet routable github enterprise server
- Disable
internet routable github enterprise addresstoggle button. - Provide
repository urlandbranch name. - Copy the
prancer runcommand from the note section. we require it during pipeline setup process
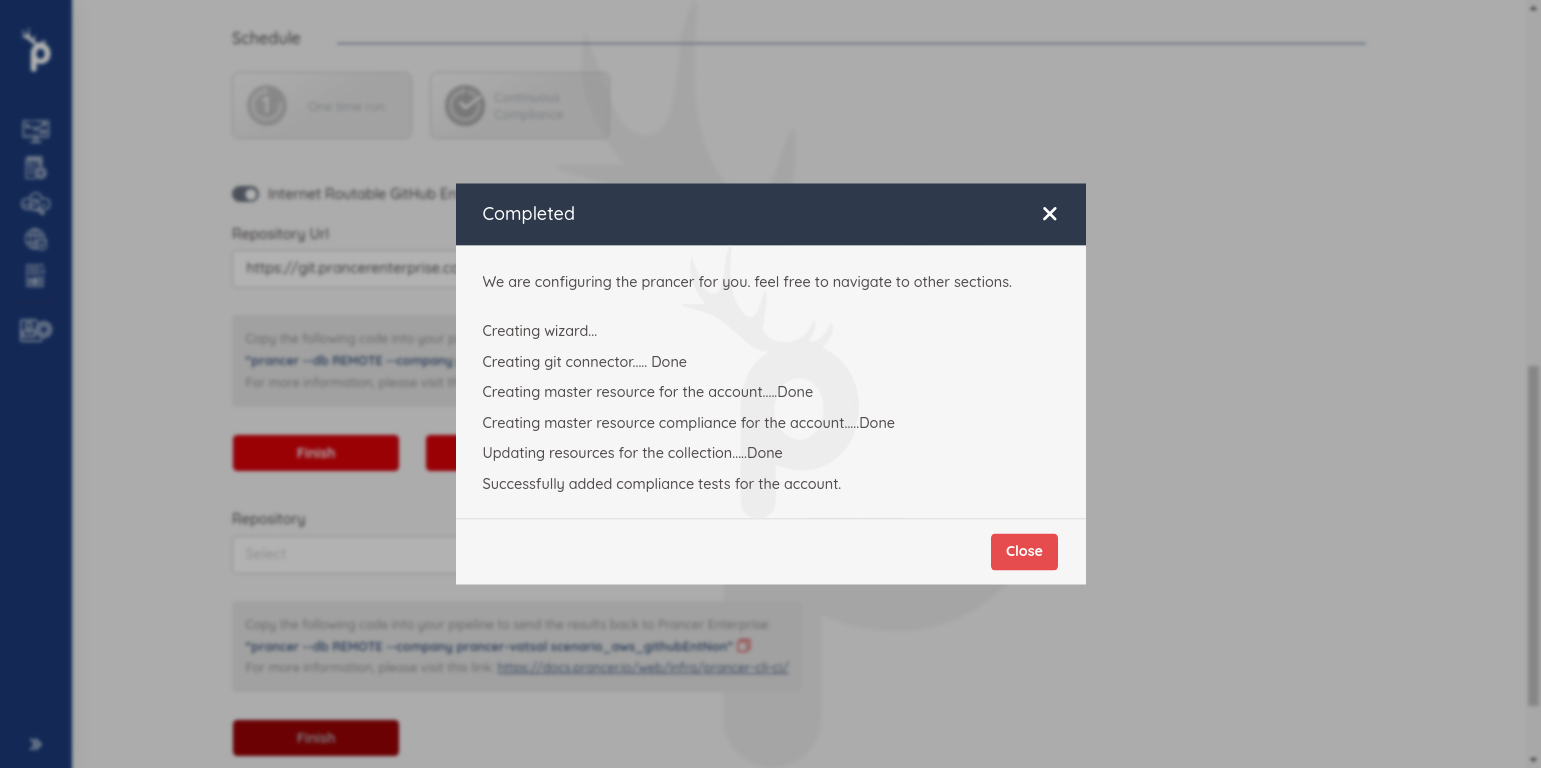
- Click on
finishbutton and new collection will be created.
Create Prancer Access Token
-
Now we will require
Prancer Access Token. to generate it do following steps.
-
Select
User Access Tokenfrom the right top menu.
-
Click
New Tokenbutton.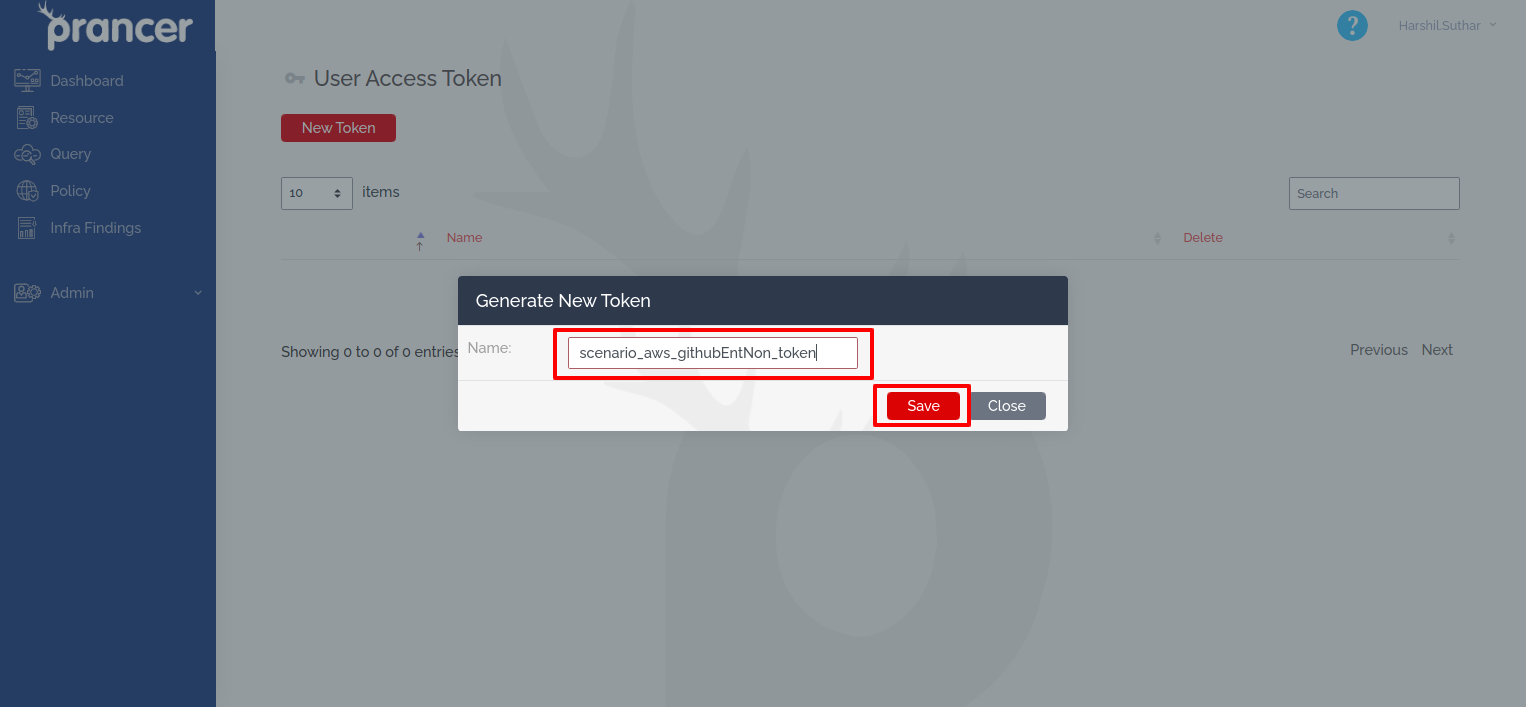
-
Provide a proper name for future identification, then click
Save.
-
Save the generated token. it will require to setup the pipeline.
Create Github Access Token
- Now we will require github enterprise
personal access tokenwith repo and user access. to get token do following steps: 
- Now go to github enterprise server and click on the profile button from the right top section and select
settingsfrom the dropdown menu.
- Select
Developer settingsfrom left sidebar.
- Select
Personal Access Tokenform left sidebar then selectGenerate New Token, it will open a form to generate a new token.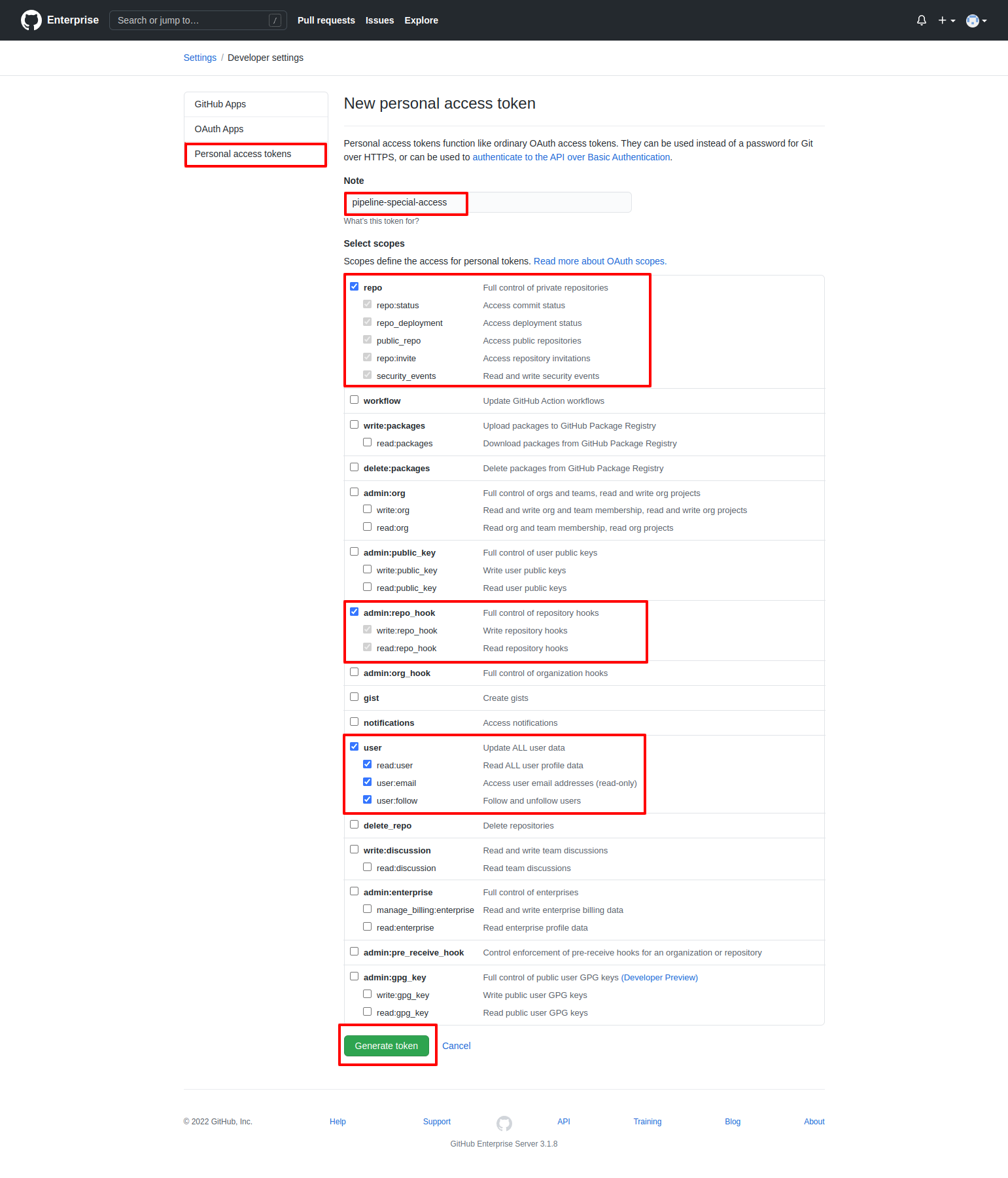
- Provide a name to token to identify it later
- Select
user,admin:repo_hookandrepowith all permissions - Then click on the
Generate Tokenbutton.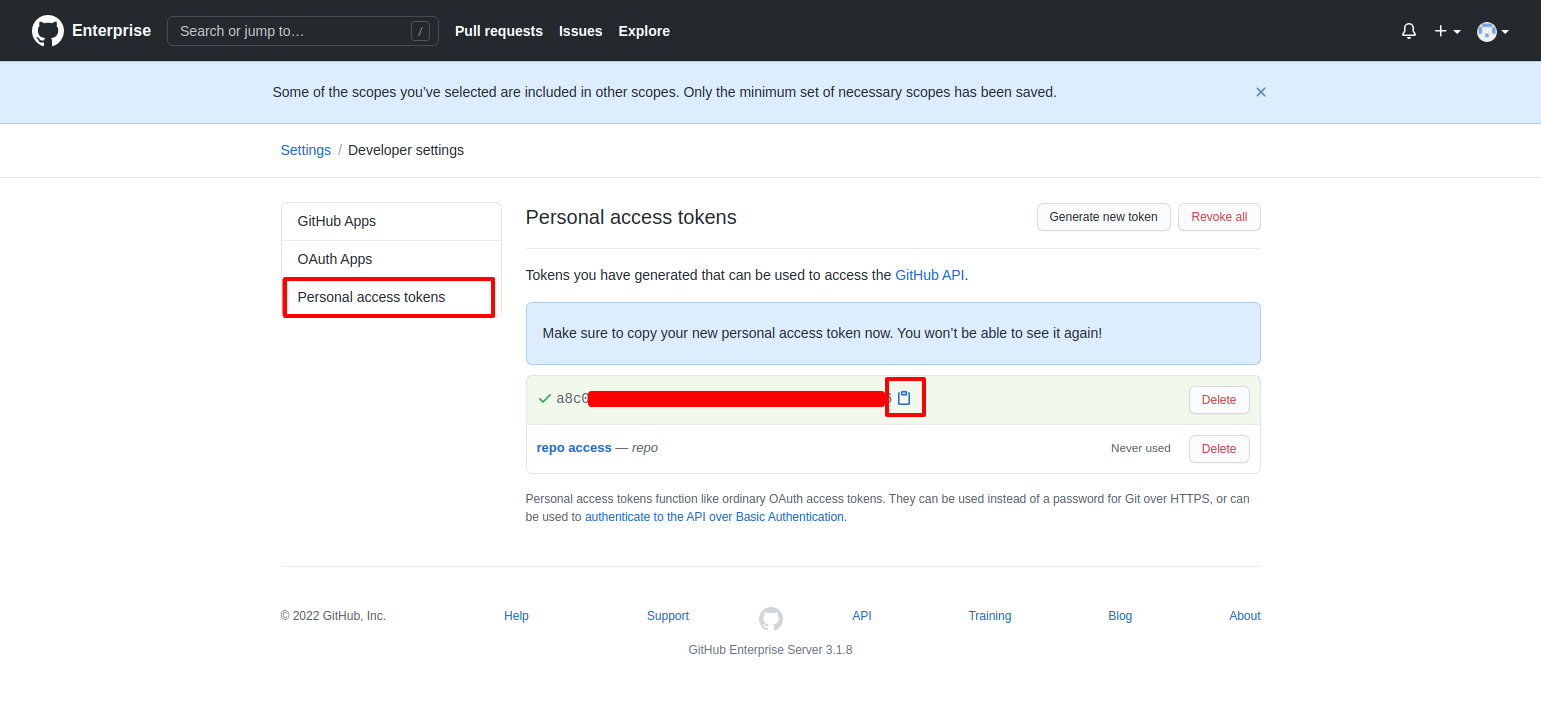
- It will generate a token as shown in above image, copy it and save it for later use.
Create Azure Pipeline
- Now have all the required items to create a pipeline for github enterprise.
- We have provided sample pipeline code for github actions and Azure Devops Pipeline.
- We will setup Azure pipeline to communicate with Github Enterprise server.
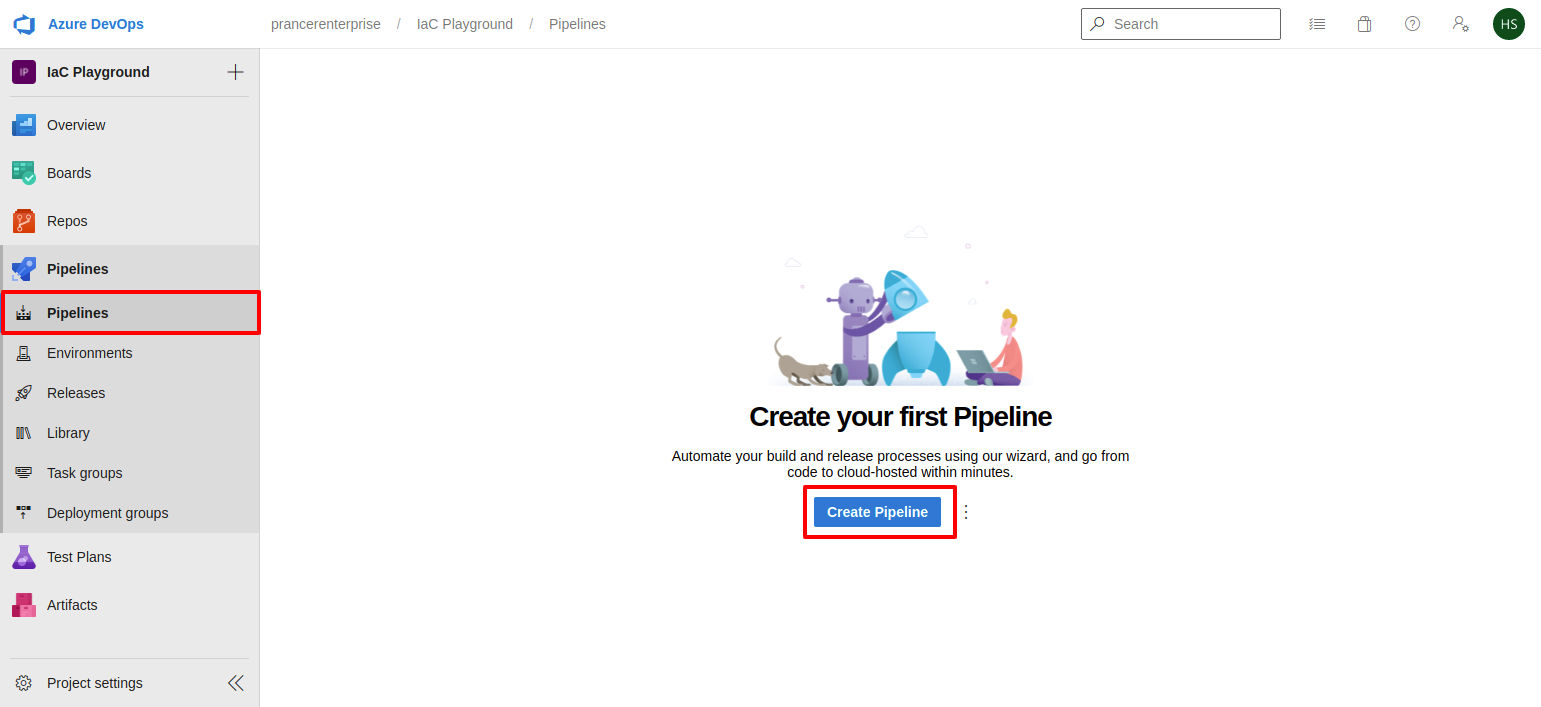
- Go to Azure Devops Account and select
Pipelinefrom left sidebar.
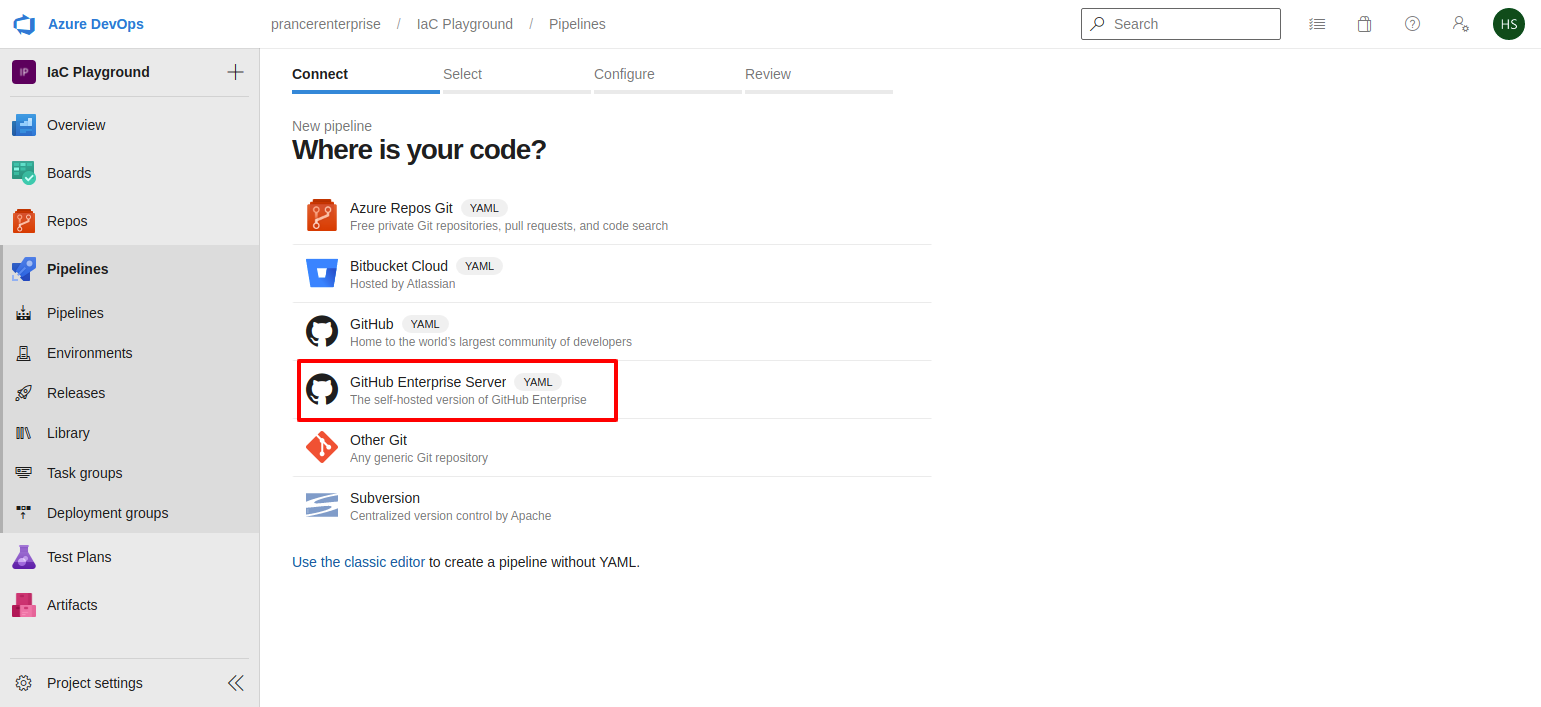
- Select
Github Enterprise Serverfrom the list
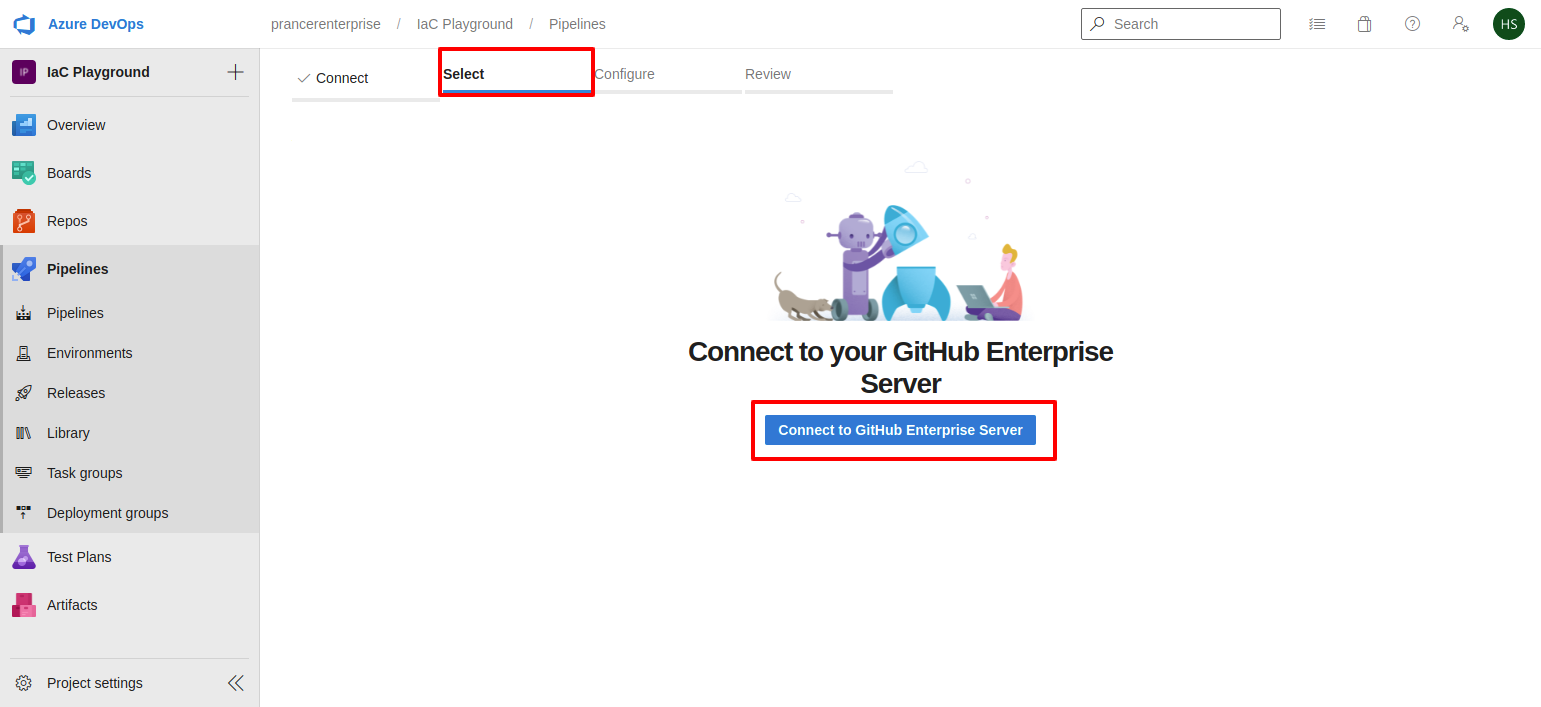
- Click on the
Connect to Github Enterprise Serverbutton to connect your github Enterprise server.
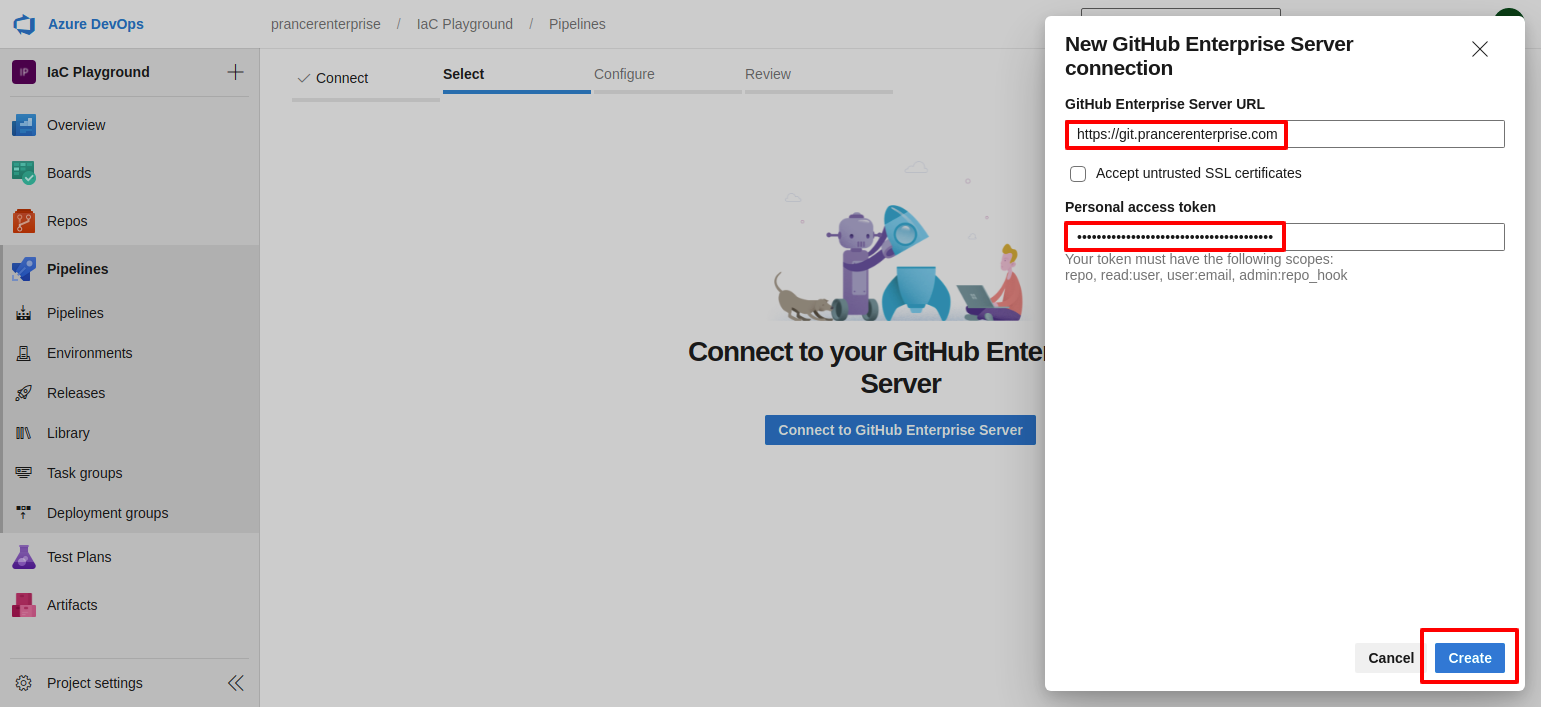
- Enter your github enterprise server URL and Github personal access token which we have generated.
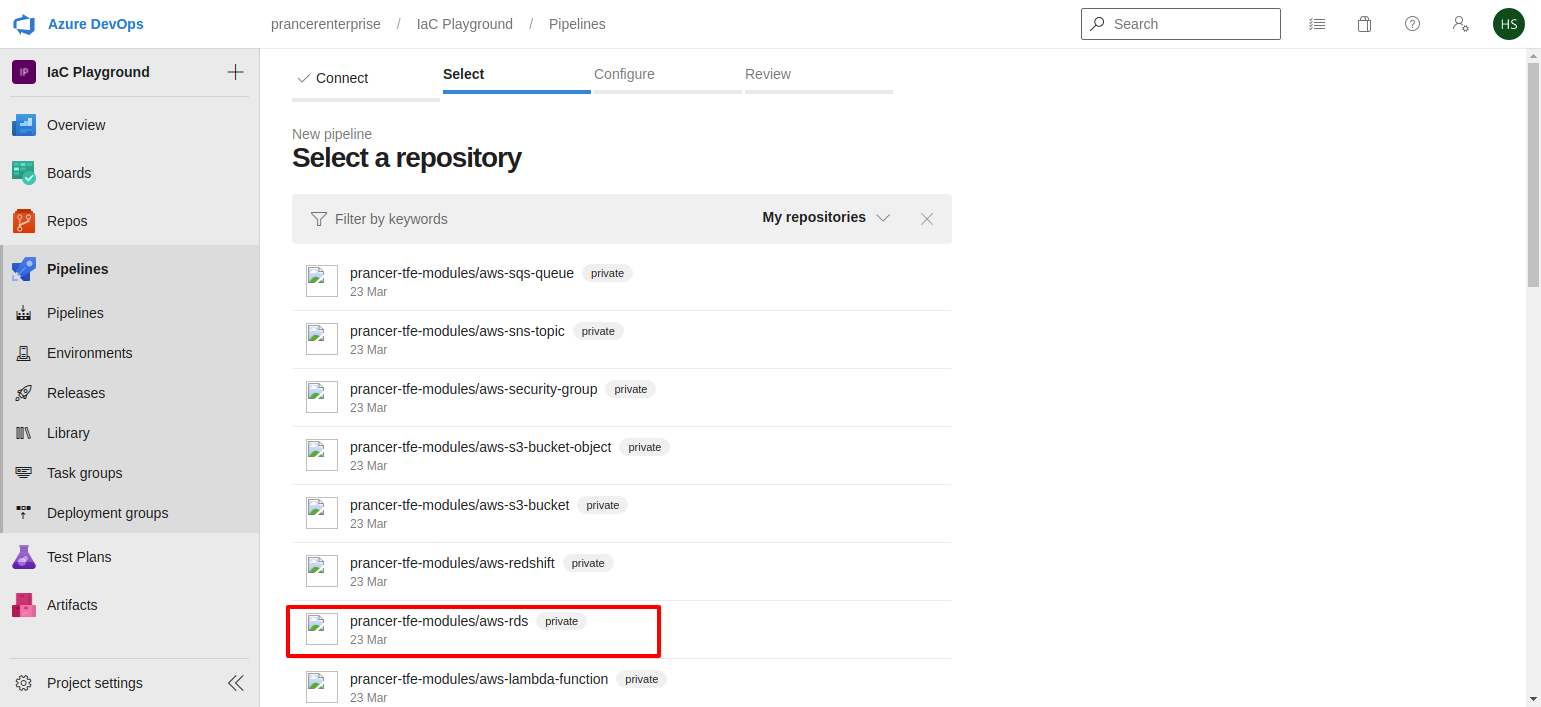
- Select the repository which you want to save the pipeline yaml file.
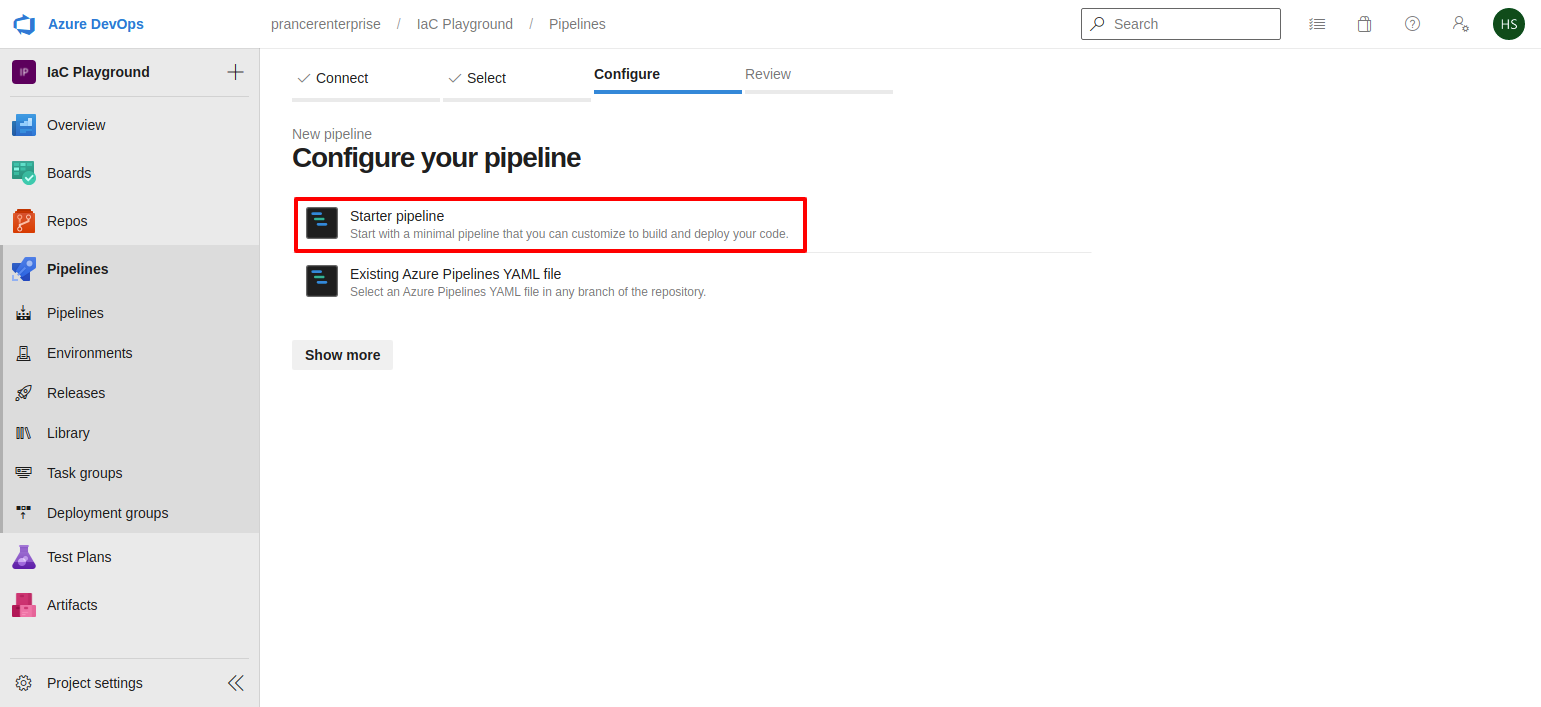
-
Select
Starter pipelineoption to setup a new pipeline. for prancer commands refer Prancer CLI -
Since the GitHub Enterprise server is non routable, user has to select a self hosted agent with an access to the GitHub Enterprise Server. Microsoft provided agents won't have access to Github Enterprise Server.
Note: Make sure to change the name of the
companyandcollectionin the following code before using it
Running prancer-basic pipeline script
trigger:
- master
resources:
- repo: self
stages:
- stage: prancer_static_code_analysis_for_iac
displayName: "Prancer Static Code Analysis for IaC"
jobs:
- job: prancer_basic
displayName: "Prancer Static Code Analysis for IaC"
pool: "Default"
steps:
- bash: |
echo "Setup start"
binary="pip3"
ispresent=`which $binary`
if [ -z $ispresent ]; then
apt-get -y install python3-pip
else
echo "using existing pip3 path: $ispresent"
fi
pip3 install -U prancer-basic
binary="opa"
ispresent=`which $binary`
if [ -z $ispresent ]; then
curl -L -o /usr/local/bin/opa https://openpolicyagent.org/downloads/v0.36.1/opa_linux_amd64_static
chmod 755 /usr/local/bin/opa
else
echo "using existing opa binary path: $ispresent"
fi
binary="helm"
ispresent=`which $binary`
if [ -z $ispresent ]; then
snap install helm --classic
else
echo "using existing helm binary path: $ispresent"
fi
export APITOKEN=${APITOKEN}
export GITTOKEN=${GITTOKEN}
prancer --db REMOTE --company liquware --apitoken "${APITOKEN}" --gittoken "${GITTOKEN}" scenario_aws_githubEntNon
env:
GITTOKEN: $(GITTOKEN)
APITOKEN: $(APITOKEN)
Running prancer-basic inside a docker image pipeline script
trigger:
- master
resources:
- repo: self
stages:
- stage: prancer_basic_setup_pipeline
displayName: "Prancer Static Code Analysis for IaC"
jobs:
- job: prancer_basic
displayName: "prancer basic install in agent"
pool: "Default"
steps:
- bash: |
echo "Setup start"
# Creating Working Directory
mkdir prancer
cd prancer
# Downloading setup.py from prancer-basic to find latest version
curl -L -o setup.py https://raw.githubusercontent.com/prancer-io/cloud-validation-framework/master/setup.py
version=`cat setup.py | grep -i 'version=' | sed -e "s/version='//" | sed -e "s/',//" | sed -e 's/ //g'`
echo $version
# Creating temp dir for opa and helm
mkdir helmdir opadir
# Download opa binary
curl -L -o opadir/opa https://openpolicyagent.org/downloads/v0.36.1/opa_linux_amd64_static
chmod 755 opadir/opa
# Download helm binary
curl -L -o helmdir/helm-v3.8.1-linux-amd64.tar.gz https://get.helm.sh/helm-v3.8.1-linux-amd64.tar.gz
tar -zxvf helmdir/helm-v3.8.1-linux-amd64.tar.gz -C helmdir
chmod 755 helmdir/linux-amd64/helm
# Creating Docker File
cat << EOF >> Dockerfile
FROM python:3.9-alpine3.15
ENV APP_VERSION=$version
RUN apk update && apk upgrade && apk add git build-base libffi-dev openssl-dev
COPY opadir/opa /usr/local/bin/opa
RUN chmod +x /usr/local/bin/opa
COPY helmdir/linux-amd64/helm /usr/local/bin/helm
RUN chmod +x /usr/local/bin/helm
RUN pip install ply
RUN pip install prancer-basic==$version
EOF
# Building Docker image with prancer-basic as per version
docker build -t prancer-basic:${version} -f Dockerfile .
# Running Prancer-basic docker image with remote for scenario_aws_githubEntNon collection
docker container run prancer-basic:${version} prancer --db REMOTE --company liquware --apitoken "${APITOKEN}" --gittoken "${GITTOKEN}" scenario_aws_githubEntNon
env:
GITTOKEN: $(GITTOKEN)
APITOKEN: $(APITOKEN)
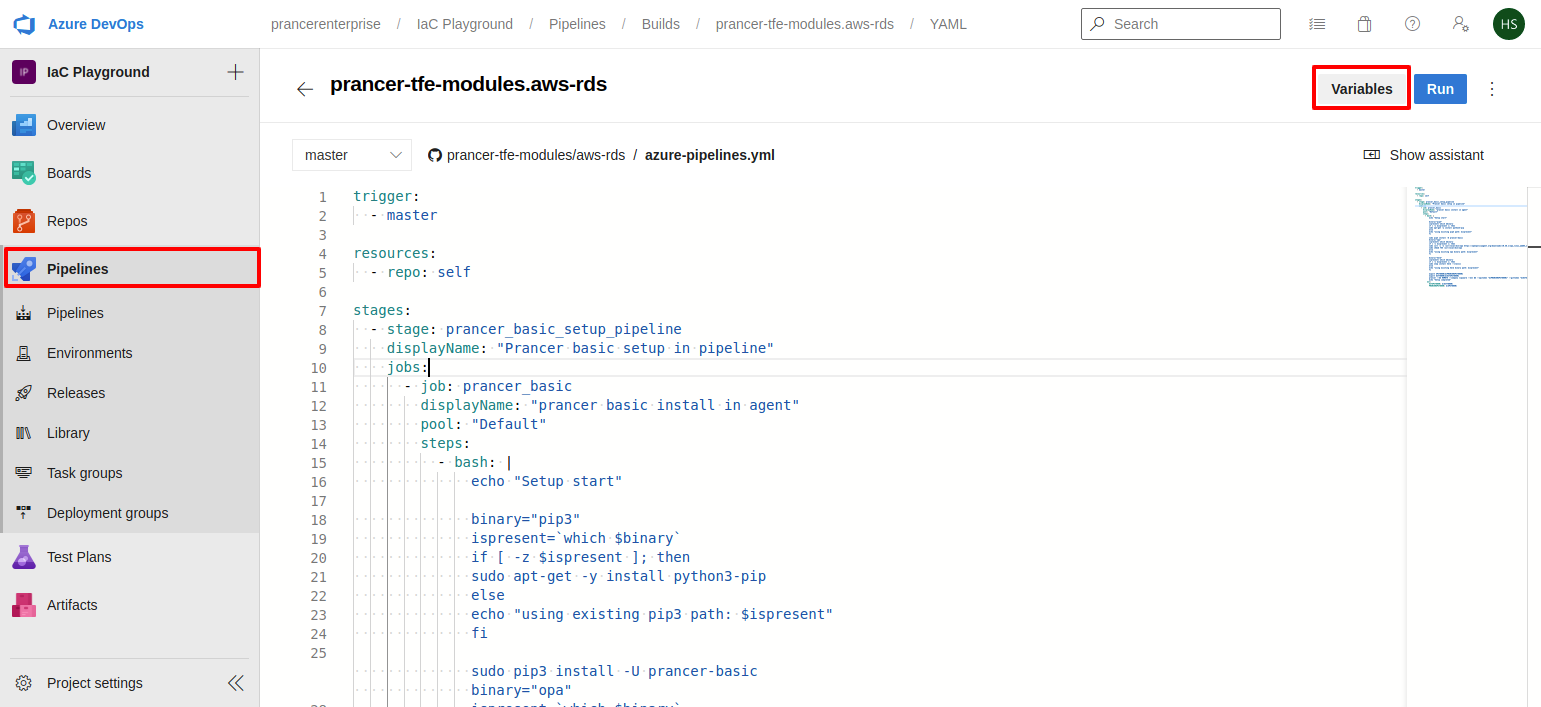
- From the Samples copy the code of Azure pipeline and peast it here then click on the
Variablesbutton from the right top corner.
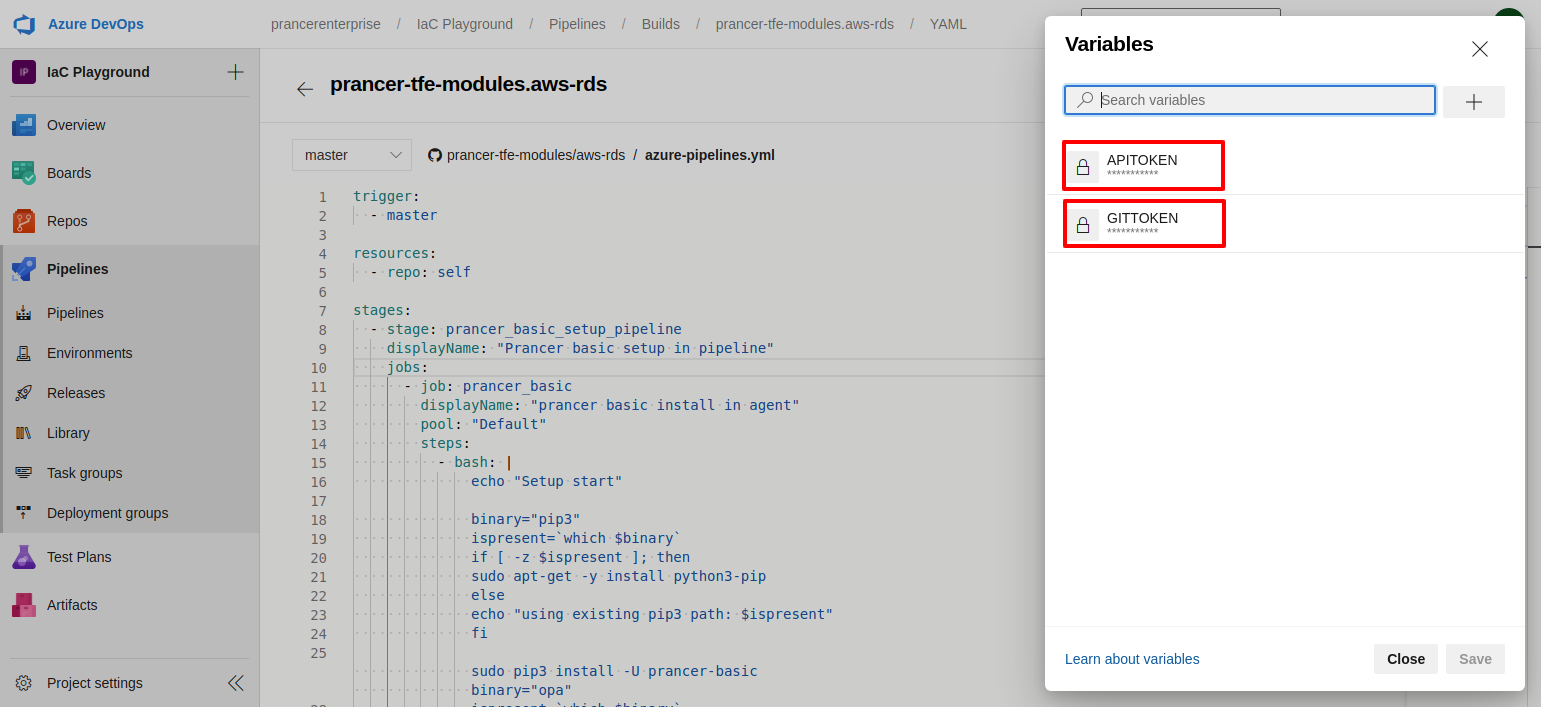
- Create above shown variables using Github Enterprise's
Personal Access Tokenwith nameGITTOKENand use Prancer'sUser Access Tokento createAPITOKENvariables.
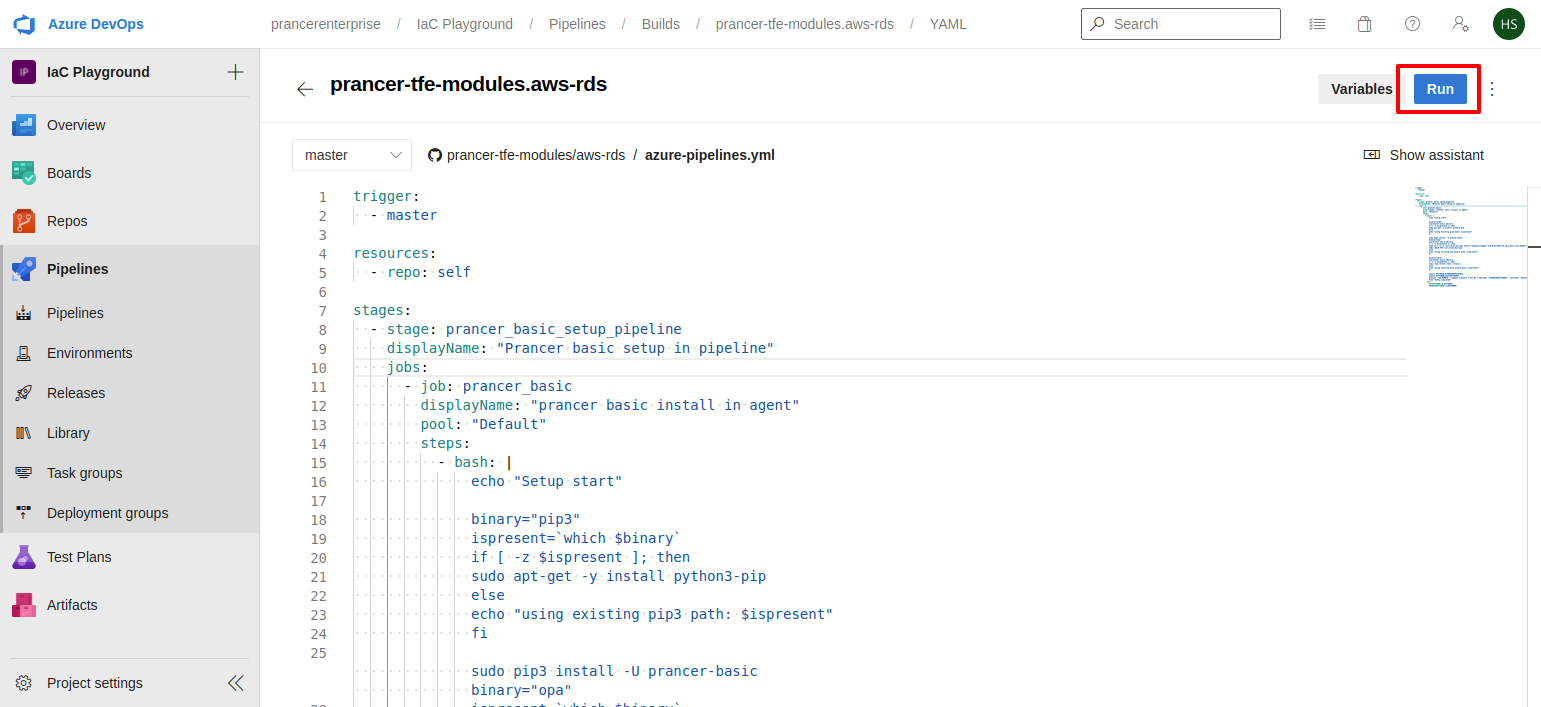
- Save an run the pipeline. the pipeline will install following items if its not available in the agnet's machine
- Pip3
- Opa
- Helm
- Prancer-basic
- Then it will run the prancer-basic and it will send output to prancer
Infra Findings.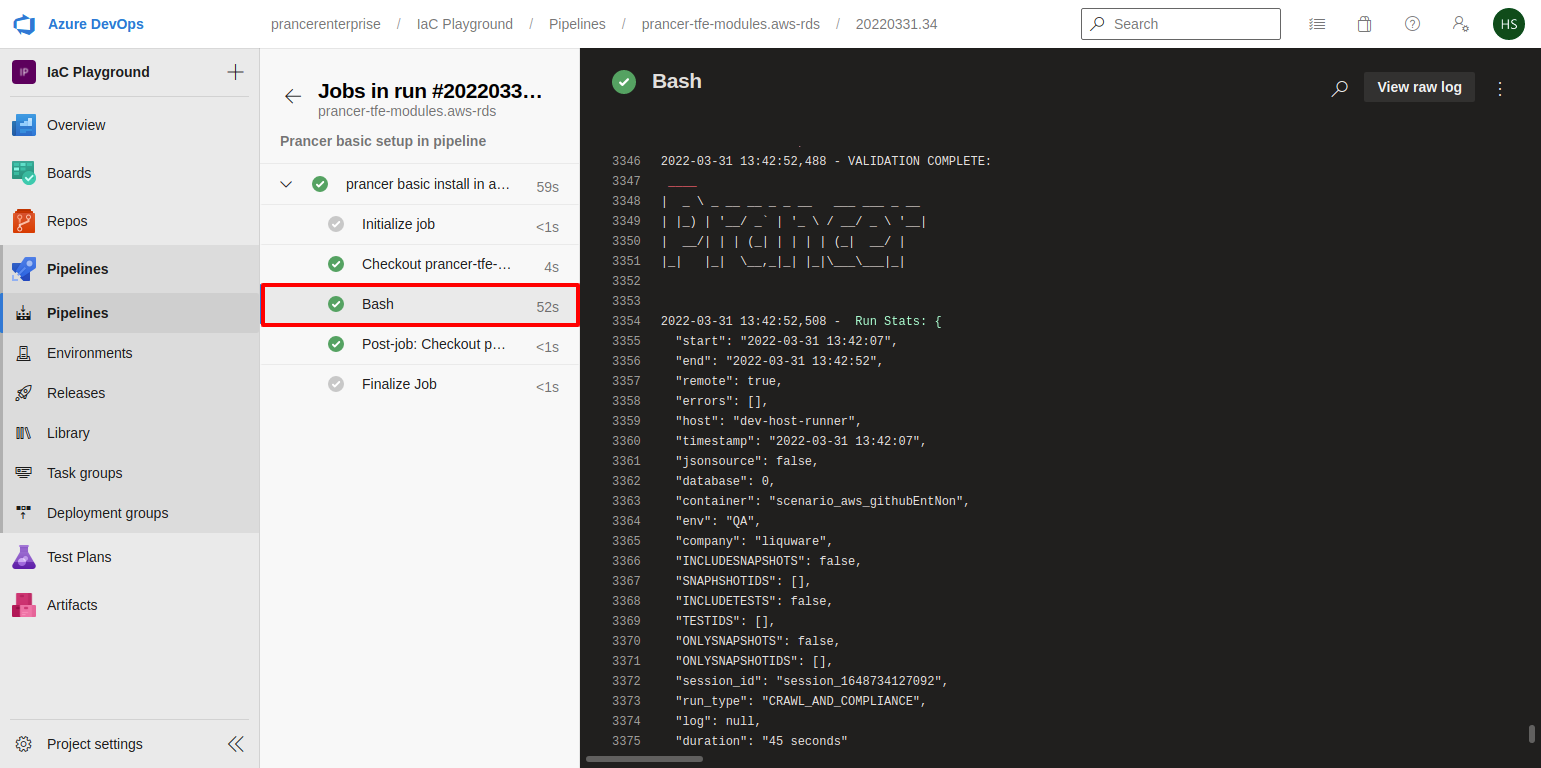
- User can check prancer logs from the pipeline output console.
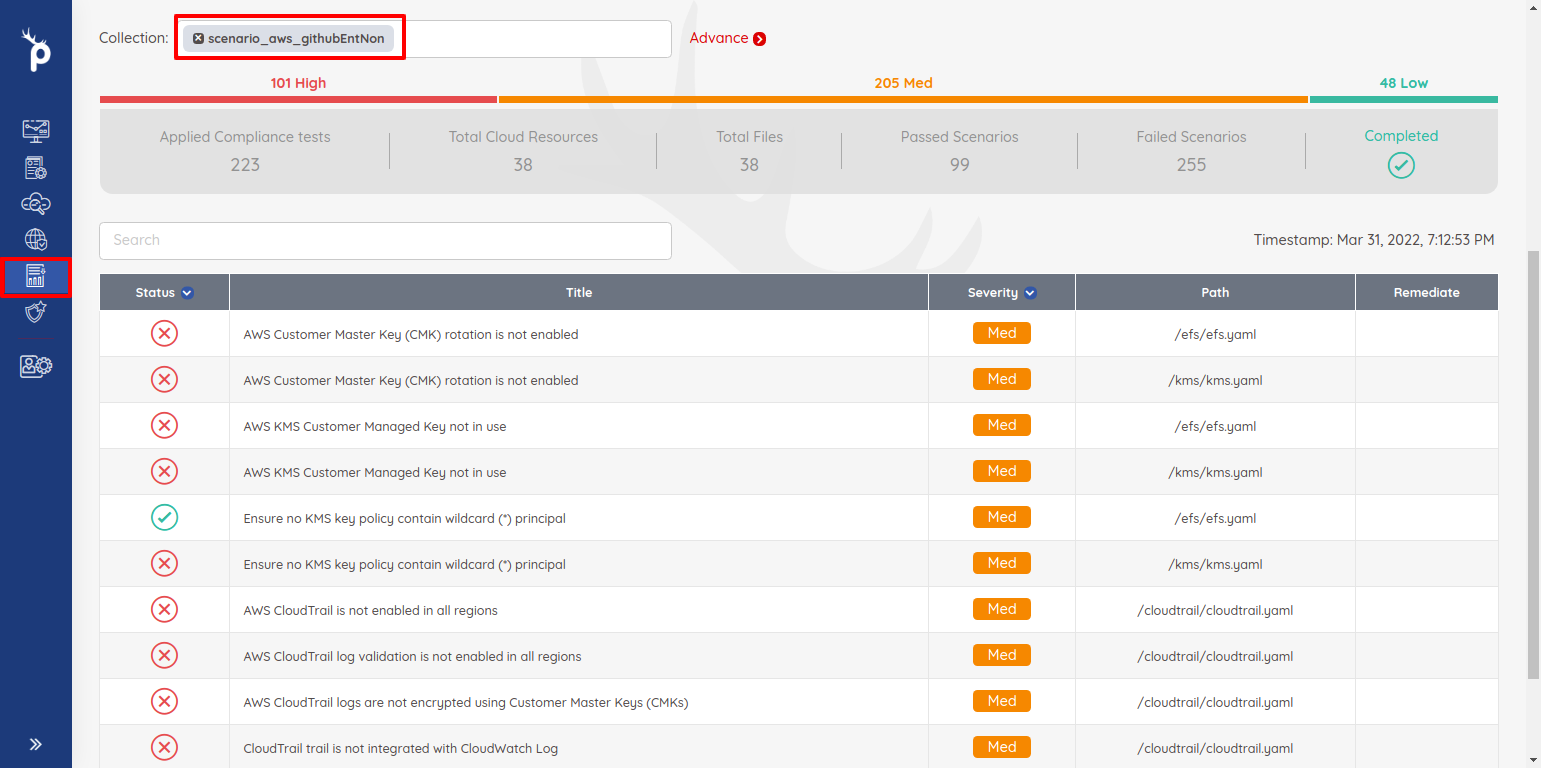
- User can checkout result from the
Infra Findingpage of the prancer portal.