Autonomous Security Wizard
Introduction
Prancer introduces a powerful feature known as the "Autonomous Security Wizard," designed to streamline the security assessment process for cloud resources. This wizard performs the following steps to automate the identification, configuration, and pentesting of cloud resources:
-
Resource Crawling: The Autonomous Security Wizard traverses all cloud resources, identifying the scope for the security assessment.
-
CSPM Testing: Once the resources are identified, the wizard conducts Cloud Security Posture Management (CSPM) tests on each resource, evaluating their adherence to security best practices and policies.
-
Pentestable Resource Identification: During this phase, the Autonomous Security Wizard isolates resources that are suitable for penetration testing based on the results of the CSPM tests.
-
PAC Config File Generation: For each identified pentestable resource, the wizard generates a corresponding PAC (Penetration testing as Code) config file. This file contains the necessary configuration details required for the subsequent penetration testing process.
-
Automated Penetration Testing: Depending on the user's preference, the Autonomous Security Wizard can also perform penetration testing on the discovered resources using the generated PAC config files. This ensures that all resources are thoroughly assessed for potential vulnerabilities.
By leveraging the Autonomous Security Wizard, developers can benefit from a streamlined, automated security assessment process for their cloud resources, ensuring comprehensive vulnerability detection and mitigation.
Step 1
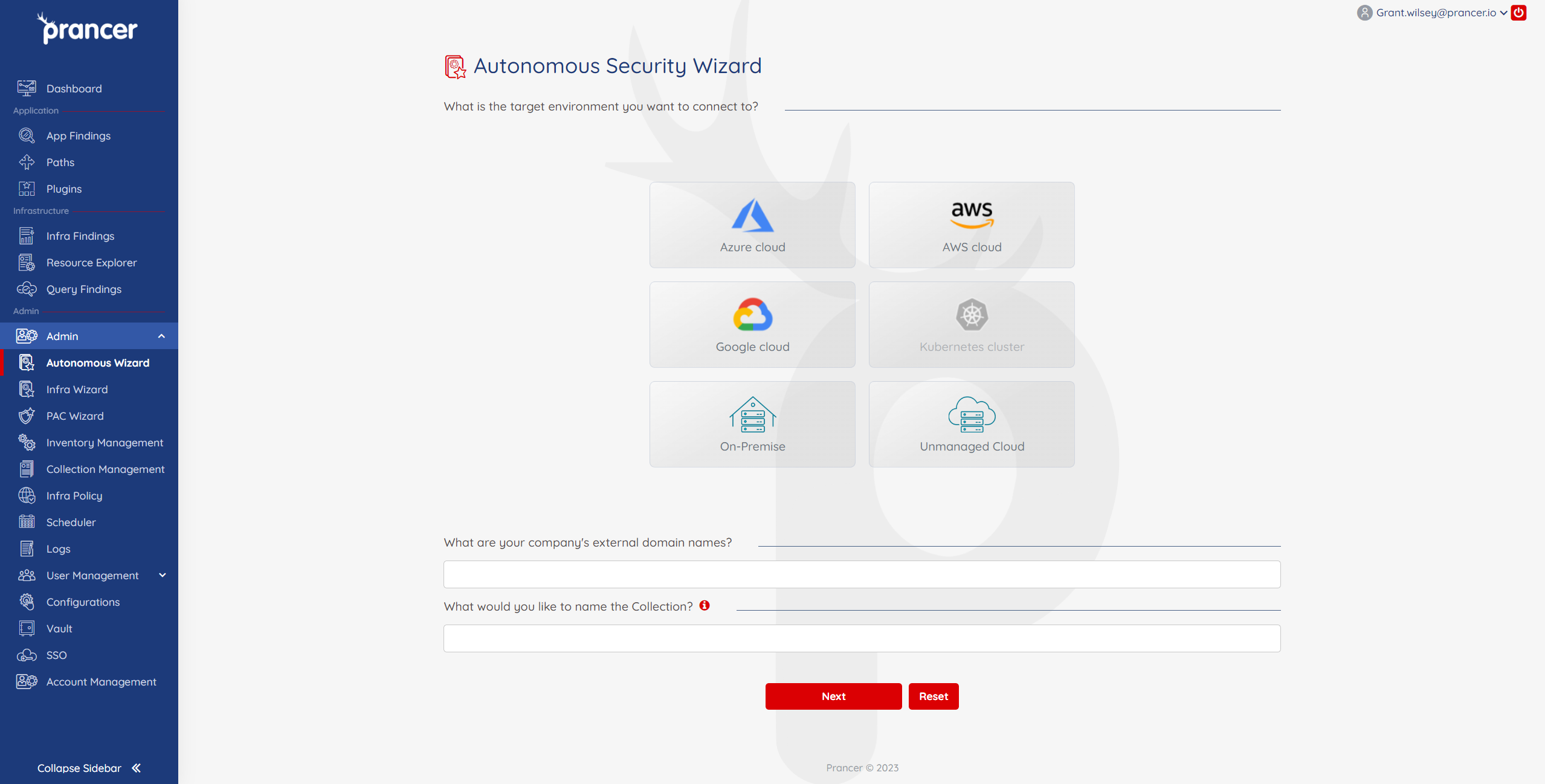
-
Choose your target environment. If the external domain is in a Cloud environment, select your specific provider and then enter your company's external domain names.
-
For On-Premise or Unmanaged Cloud, you will be prompted on the next screen to enter the IP address range to include and exclude in the scan.
-
Give the Collection an appropriate name and then proceed to Step 2 to enter the cloud connection details.
- When filling external domain, be sure to specify
http://orhttps://
- When filling external domain, be sure to specify
Step 2
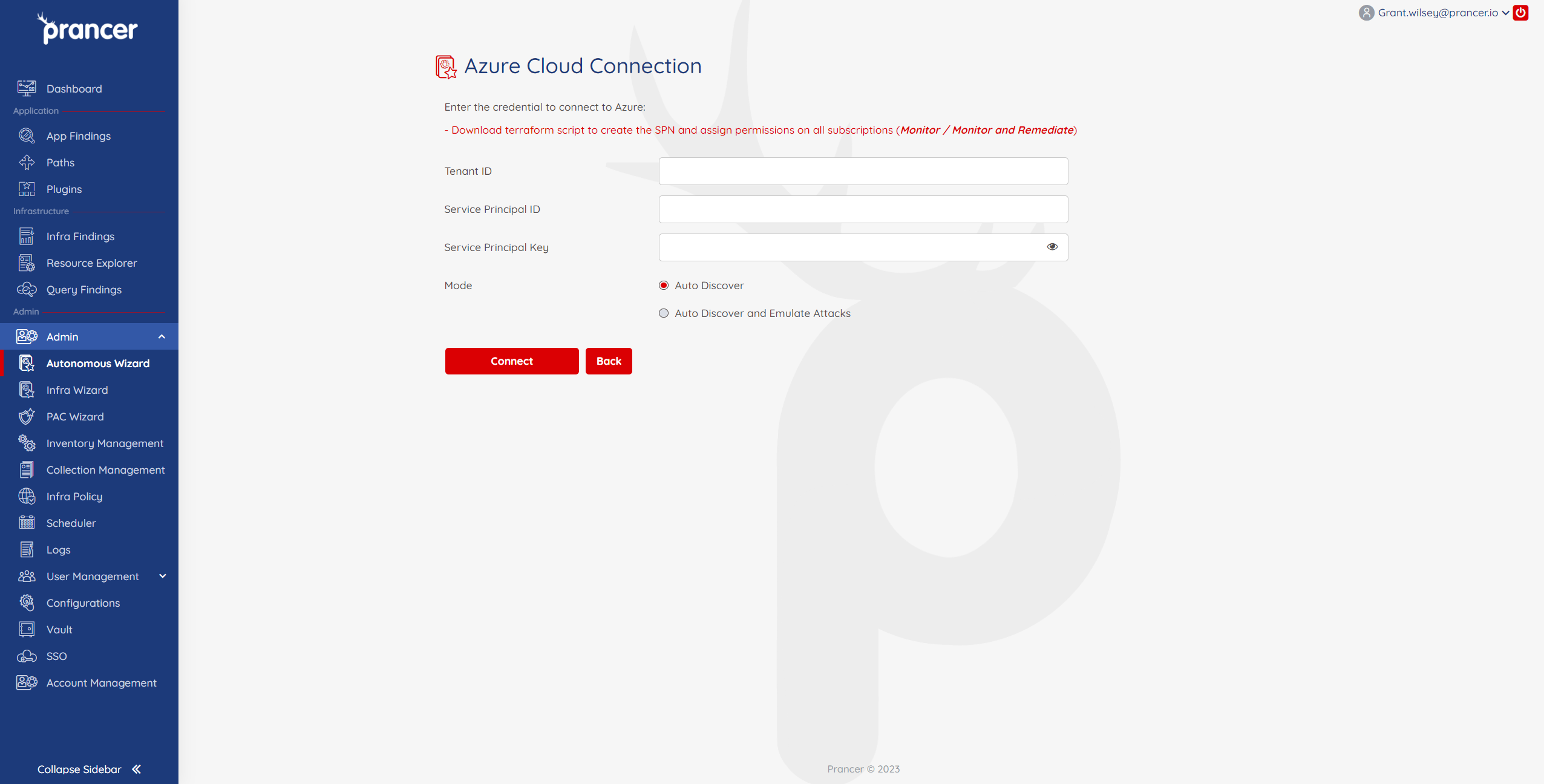
- Enter in your cloud provider details and then select
Auto DiscoverorAuto Discover and Emulate AttacksAuto Discover- This will search for subdomains and assets that are in scope of the test.Auto Discover and Emulate Attacks- In addition to discovering subdomains in scope, the Autonomous Wizard will actively test against the targets. It is recommended to run Discovery first to ensure desired targets are in scope of the test.
Once connected, the process will begin and you will guided to the collections page in Collection Management. Your cloud connectors will be visibile in the collection if there is a cloud connector already associated with it.
To review the discovered targets, PAC files, connector configuration files, and to start a PenTest, navigate to the Inventory Management. If the Emulate Attacks option was selected, this is also where you can review the progress of the test.